The Future Is Purple
Too Many Tools? Too Much Cost? Let’s Fix That.
The Average Enteprise Security Team Juggles 76 Different Tools
The Average Enterprise Spends $5.7 Million Annually on Cybersecurity
Yet 68% of Organizations Struggle to Remediate Critical Vulnerabilities on Time
See How CyberOptix Addresses These Problems
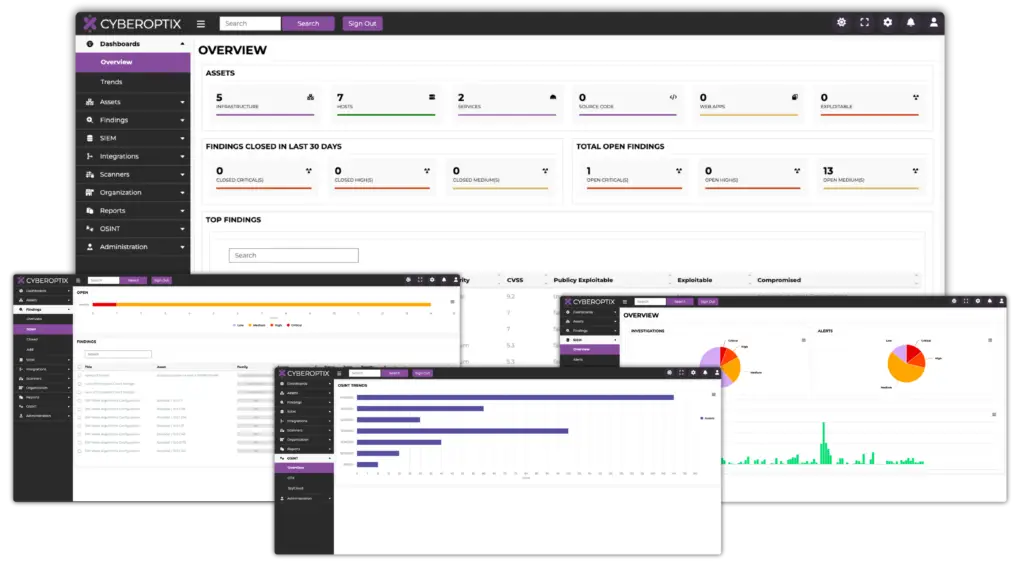

Streamline Cybersecurity Operations and Collaboration
Running an effective vulnerability management program can feel overwhelming when you’re juggling an unnecessary amount of tools and platforms. Unfortunately, many organizations do just this, with the average enterprise security team juggling 76 separate cybersecurity tools, resulting in a disjointed vulnerability management program that delays remediation and reduces collaboration between offensive and defensive teams.
Adding more tools or increasing budgets rarely solves the problem. Instead, the solution lies in purple teaming, a strategy that fosters collaboration in order to strengthen your security posture. That’s where CyberOptix comes in.
With CyberOptix, you can bring your offensive and defensive teams together, reduce cost, and focus on what matters most: protecting your organization.
Explore CyberOptix on Your Own
Reduce Your Exposure by Addressing a Wide Array of Threats From One Platform
From misconfigurations to supply chain risk, and stolen credentials to leaky buckets, CyberOptix allows your security team to address a wide variety of threats and attack vectors from one location.
Lower Operational Cost by Consolidating Five Key Cybersecurity Solutions
CyberOptix consolidates five core cybersecurity solutions into one platform, centralizing your vulnerability management program, reducing overall cost, and simplifying processes.
Improve Red and Blue Team Collaboration Through Purple Teaming
CyberOptix is designed with use cases for both red and blue teams in mind, enabling your entire security team to use purple teaming to collaboratively identify and remediate vulnerabilities.
Trusted By

“Penetration testing is often a high-pressure role—every vulnerability we find can make or break a client’s defenses. With the CyberOptix platform, I can organize findings in a centralized dashboard, validate vulnerabilities with ease, and ensure the results are automatically distributed to the client’s security team members based on their roles. This eliminates confusion and accelerates remediation.”

Elliot ThompsonPenetration Tester at TrollEye Security
“As someone who’s managed cybersecurity at various enterprises, I’ve seen firsthand how disjointed tools can hinder both operations and team collaboration. When I started at TrollEye Security, the CyberOptix platform immediately caught my attention. Its ability to consolidate vulnerability insights and align them with the right roles on a client’s security team was a game-changer.
With CyberOptix, my team can quickly identify vulnerabilities, validate them efficiently, and distribute tailored recommendations without the typical back-and-forth. This streamlining has saved us countless hours and allowed us to focus on proactive security measures rather than chasing down information. CyberOptix doesn’t just organize operations—it brings teams together to operate as a cohesive unit. For any organization looking to improve cybersecurity effectiveness, this platform is a must-have.”

Matthew BallardCybersecurity Services Manager at TrollEye Security
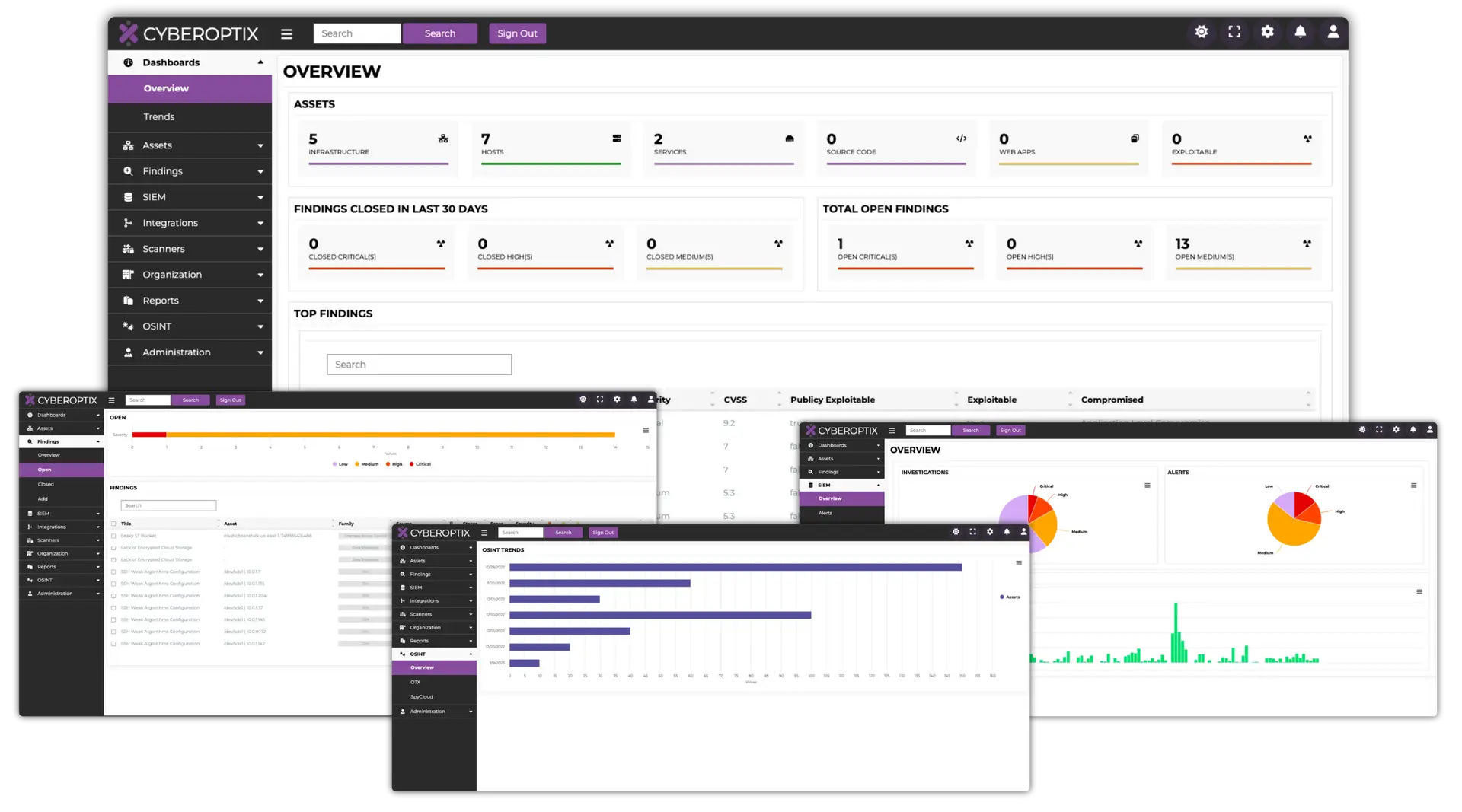
CyberOptix’s Licenses
The CyberOptix Platform offers five distinct licenses, all of which are designed to bridge the gap between offensive and defensive teams, helping them to collaboratively identify and remediate vulnerabilities.
Each license addresses a specific set of threats, and provides your security team with a unique set of tools to address them.
Wether you struggle with remediating dark web threats, securing your software, or reducing vulnerabilities in your cloud infrastructure, we have a license that can help you.
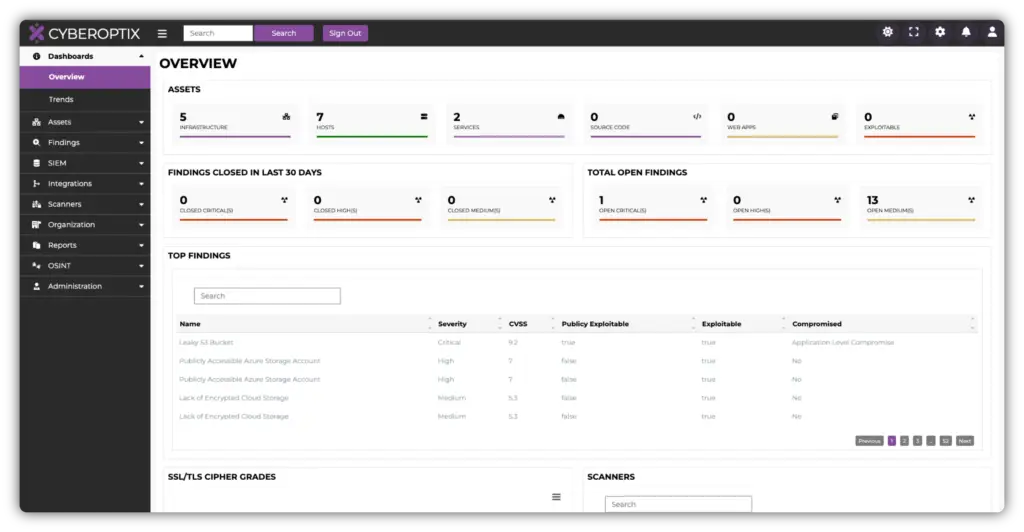
How Offensive Teams Use CyberOptix’s Penetration Testing Management License
The Penetration Testing Management License serves as the foundation for offensive security teams to identify vulnerabilities, conduct targeted penetration tests, and refine their strategies.
-
Perform detailed scans across networks, hosts, and web applications, uncovering weaknesses and entry points. -
Integrate with tools like Metasploit, Nmap, and GVM to simulate attacks and test vulnerabilities effectively. -
Use the kanban board and findings management system to document vulnerabilities and plan attack scenarios.
Learn More About Penetration Testing Management
How Defensive Teams Use CyberOptix’s Penetration Testing Management License
Defensive teams utilize the Penetration Testing Management License to gain a clear understanding of vulnerabilities within their organization’s infrastructure.
-
Identify and track vulnerabilities across systems to ensure no risks are overlooked. -
Track vulnerability remediation through the kanban board interface. -
Leverage role-based task distribution and actionable reports to accelerate remediation time.

Learn More About Penetration Testing Management
How Offensive Teams Use Attack Surface Management
CyberOptix’s Attack Surface Management License provides offensive teams with visibility into both internal and external vulnerabilities, allowing them to craft realistic attack scenarios.
-
Identify vulnerabilities across cloud and on-premises systems to simulate potential attack scenarios. -
Evaluate misconfigurations and exploitable gaps in cloud systems that could be leveraged by attackers. -
Leverage ASM’s asset discovery and detailed insights to pinpoint high-risk paths that attackers might exploit.

Learn More About The Attack Surface Management License
How Defensive Teams Use Attack Surface Management
Defensive teams use CyberOptix’s Attack Surface Management License to gain a comprehensive view of their attack surface, enabling them to identify and close security gaps proactively.
-
Gain a clear inventory of internal and external assets, reducing blind spots in the attack surface. -
Identify and resolve misconfigurations and vulnerabilities before attackers can exploit them. -
Use detailed reports to inform patching, mitigation, and long-term security strategies.

Learn More About The Attack Surface Management License
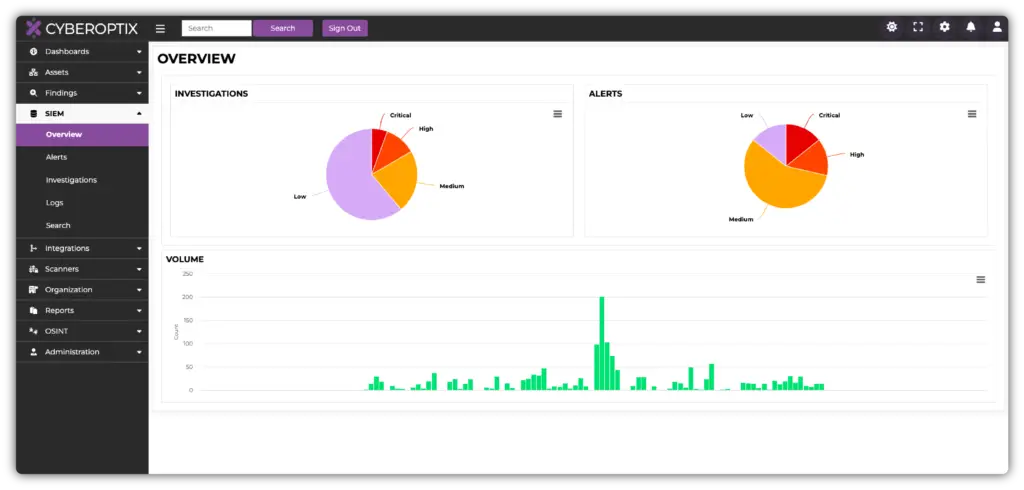
How Offensive Teams Use SIEM
The CyberOptix’s SIEM License empowers offensive teams to conduct advanced simulations and test an organization’s defenses by leveraging real-time insights into logs and security events.
-
Use real-time log data to test how well an organization’s defenses respond to simulated attacks. -
Analyze the visibility of offensive activities to better understand detection and improve methodologies. -
Work alongside defensive teams in controlled simulations to uncover vulnerabilities and strengthen defenses.
How Defensive Teams Use SIEM
Defensive teams rely on CyberOptix’s SIEM License to gain real-time visibility into security events and logs, enabling them to detect and respond to threats with speed and accuracy.
-
Monitor security events and logs to identify and respond to threats as they occur. -
Leverage insights from purple teaming simulations to strengthen defensive strategies and close security gaps. -
Use correlated log data to prioritize and accelerate responses to potential breaches, reducing overall risk.
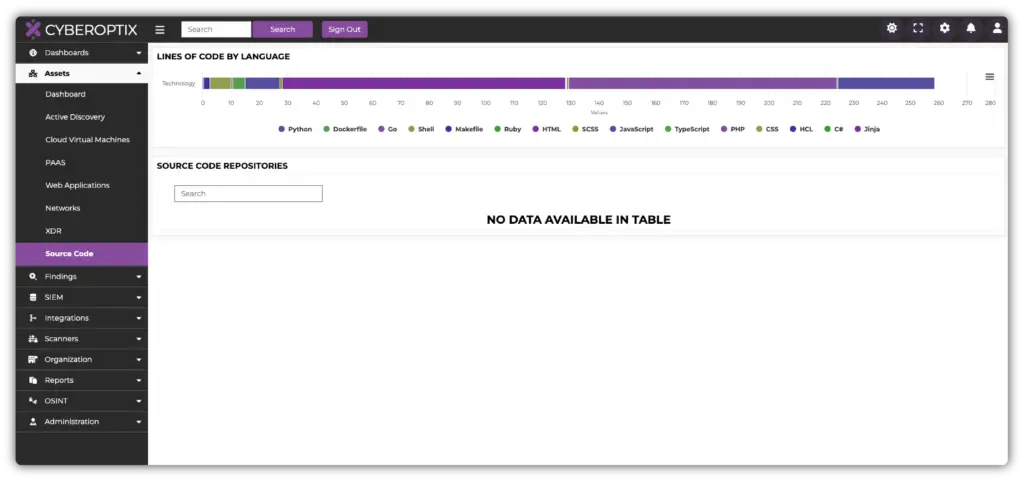
How Offensive Teams Use DevSecOps
Offensive teams leverage CyberOptix’s DevSecOps License to uncover application vulnerabilities with precision, enabling targeted and comprehensive penetration testing.
-
Identify vulnerabilities in applications through SAST, DAST, and repository integrations, focusing on exploitable code. -
Leverage vulnerability data to design more precise and realistic penetration testing strategies. -
Provide detailed insights into exploitable weaknesses to improve code security during development.
How Defensive Teams Use DevSecOps
Defensive teams rely on CyberOptix’s DevSecOps License to seamlessly integrate security into the Software Development Lifecycle (SDLC), ensuring vulnerabilities are identified and mitigated early, before they reach production.
-
Monitor and resolve risks directly within the CI/CD pipeline and source code repositories. -
Seamlessly connect with tools like GitHub and Snyk to address risks as part of the development workflow. -
Focus on high-priority vulnerabilities to reduce the attack surface and ensure secure code deployment.
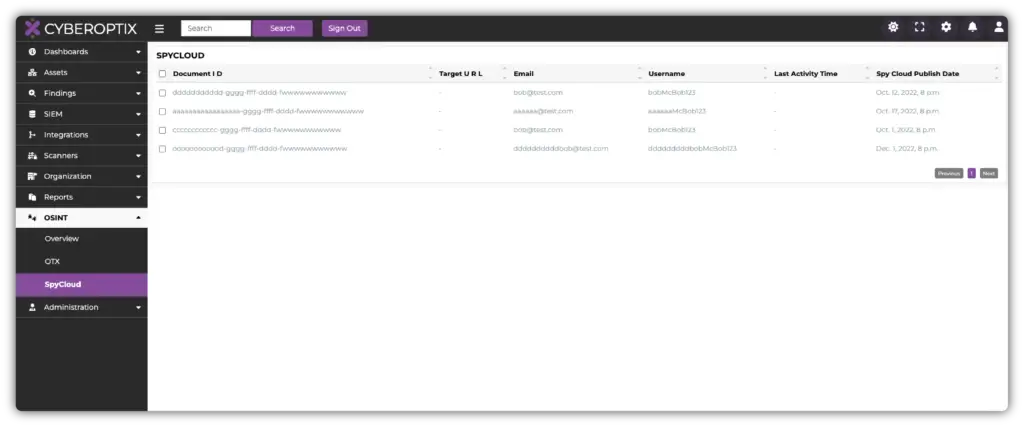
How Offensive Teams Use Dark Web Monitoring
Offensive teams use CyberOptix’s Dark Web License to simulate real-world attack scenarios, leveraging intelligence gathered from dark web sources.
-
Use intelligence from exposed credentials and breach data to simulate potential threat actor activities. -
Analyze third-party vulnerabilities and executive exposures to uncover new attack vectors. -
Provide insights from simulations that help defensive teams address gaps revealed through dark web intelligence.
Learn More About Dark Web Monitoring
How Defensive Teams Use Dark Web Monitoring
Defensive teams rely on CyberOptix’s Dark Web License to proactively address risks identified on the dark web, such as stolen credentials, vendor breach records, and executive exposure.
-
Identify and reset stolen credentials to prevent unauthorized access. -
Monitor and mitigate risks associated with executive data exposure on the dark web. -
Identify and assess vulnerabilities in vendor breach data to minimize supply chain threats.

Learn More About Dark Web Monitoring
How Offensive Teams Use CyberOptix’s Penetration Testing Management License
The Penetration Testing Management License serves as the foundation for offensive security teams to identify vulnerabilities, conduct targeted penetration tests, and refine their strategies.
-
Perform detailed scans across networks, hosts, and web applications, uncovering weaknesses and entry points. -
Integrate with tools like Metasploit, Nmap, and GVM to simulate attacks and test vulnerabilities effectively. -
Use the kanban board and findings management system to document vulnerabilities and plan attack scenarios.

Learn More About Penetration Testing Management
How Defensive Teams Use CyberOptix’s Penetration Testing Management License
Defensive teams utilize the Penetration Testing Management License to gain a clear understanding of vulnerabilities within their organization’s infrastructure.
-
Identify and track vulnerabilities across systems to ensure no risks are overlooked. -
Track vulnerability remediation through the kanban board interface. -
Leverage role-based task distribution and actionable reports to accelerate remediation time.

Learn More About Penetration Testing Management
How Offensive Teams Use CyberOptix’s Penetration Testing Management License
The Penetration Testing Management License serves as the foundation for offensive security teams to identify vulnerabilities, conduct targeted penetration tests, and refine their strategies.
-
Perform detailed scans across networks, hosts, and web applications, uncovering weaknesses and entry points. -
Integrate with tools like Metasploit, Nmap, and GVM to simulate attacks and test vulnerabilities effectively. -
Use the kanban board and findings management system to document vulnerabilities and plan attack scenarios.

Learn More About Penetration Testing Management
How Defensive Teams Use CyberOptix’s Penetration Testing Management License
Defensive teams utilize the Penetration Testing Management License to gain a clear understanding of vulnerabilities within their organization’s infrastructure.
-
Identify and track vulnerabilities across systems to ensure no risks are overlooked. -
Track vulnerability remediation through the kanban board interface. -
Leverage role-based task distribution and actionable reports to accelerate remediation time.

Learn More About Penetration Testing Management
How Offensive Teams Use Attack Surface Management
CyberOptix’s Attack Surface Management License provides offensive teams with visibility into both internal and external vulnerabilities, allowing them to craft realistic attack scenarios.
-
Identify vulnerabilities across cloud and on-premises systems to simulate potential attack scenarios. -
Evaluate misconfigurations and exploitable gaps in cloud systems that could be leveraged by attackers. -
Leverage ASM’s asset discovery and detailed insights to pinpoint high-risk paths that attackers might exploit.

Learn More About The Attack Surface Management License
How Defensive Teams Use Attack Surface Management
Defensive teams use CyberOptix’s Attack Surface Management License to gain a comprehensive view of their attack surface, enabling them to identify and close security gaps proactively.
-
Gain a clear inventory of internal and external assets, reducing blind spots in the attack surface. -
Identify and resolve misconfigurations and vulnerabilities before attackers can exploit them. -
Use detailed reports to inform patching, mitigation, and long-term security strategies.

Learn More About The Attack Surface Management License
How Offensive Teams Use Attack Surface Management
CyberOptix’s Attack Surface Management License provides offensive teams with visibility into both internal and external vulnerabilities, allowing them to craft realistic attack scenarios.
-
Identify vulnerabilities across cloud and on-premises systems to simulate potential attack scenarios. -
Evaluate misconfigurations and exploitable gaps in cloud systems that could be leveraged by attackers. -
Leverage ASM’s asset discovery and detailed insights to pinpoint high-risk paths that attackers might exploit.

Learn More About The Attack Surface Management License
How Defensive Teams Use Attack Surface Management
Defensive teams use CyberOptix’s Attack Surface Management License to gain a comprehensive view of their attack surface, enabling them to identify and close security gaps proactively.
-
Gain a clear inventory of internal and external assets, reducing blind spots in the attack surface. -
Identify and resolve misconfigurations and vulnerabilities before attackers can exploit them. -
Use detailed reports to inform patching, mitigation, and long-term security strategies.

Learn More About The Attack Surface Management License
How Offensive Teams Use SIEM
The CyberOptix’s SIEM License empowers offensive teams to conduct advanced simulations and test an organization’s defenses by leveraging real-time insights into logs and security events.
-
Use real-time log data to test how well an organization’s defenses respond to simulated attacks. -
Analyze the visibility of offensive activities to better understand detection and improve methodologies. -
Work alongside defensive teams in controlled simulations to uncover vulnerabilities and strengthen defenses.
How Defensive Teams Use SIEM
Defensive teams rely on CyberOptix’s SIEM License to gain real-time visibility into security events and logs, enabling them to detect and respond to threats with speed and accuracy.
-
Monitor security events and logs to identify and respond to threats as they occur. -
Leverage insights from purple teaming simulations to strengthen defensive strategies and close security gaps. -
Use correlated log data to prioritize and accelerate responses to potential breaches, reducing overall risk.
How Offensive Teams Use SIEM
The CyberOptix’s SIEM License empowers offensive teams to conduct advanced simulations and test an organization’s defenses by leveraging real-time insights into logs and security events.
-
Use real-time log data to test how well an organization’s defenses respond to simulated attacks. -
Analyze the visibility of offensive activities to better understand detection and improve methodologies. -
Work alongside defensive teams in controlled simulations to uncover vulnerabilities and strengthen defenses.
How Defensive Teams Use SIEM
Defensive teams rely on CyberOptix’s SIEM License to gain real-time visibility into security events and logs, enabling them to detect and respond to threats with speed and accuracy.
-
Monitor security events and logs to identify and respond to threats as they occur. -
Leverage insights from purple teaming simulations to strengthen defensive strategies and close security gaps. -
Use correlated log data to prioritize and accelerate responses to potential breaches, reducing overall risk.
How Offensive Teams Use DevSecOps
Offensive teams leverage CyberOptix’s DevSecOps License to uncover application vulnerabilities with precision, enabling targeted and comprehensive penetration testing.
-
Identify vulnerabilities in applications through SAST, DAST, and repository integrations, focusing on exploitable code. -
Leverage vulnerability data to design more precise and realistic penetration testing strategies. -
Provide detailed insights into exploitable weaknesses to improve code security during development.
How Defensive Teams Use DevSecOps
Defensive teams rely on CyberOptix’s DevSecOps License to seamlessly integrate security into the Software Development Lifecycle (SDLC), ensuring vulnerabilities are identified and mitigated early, before they reach production.
-
Monitor and resolve risks directly within the CI/CD pipeline and source code repositories. -
Seamlessly connect with tools like GitHub and Snyk to address risks as part of the development workflow. -
Focus on high-priority vulnerabilities to reduce the attack surface and ensure secure code deployment.
How Offensive Teams Use DevSecOps
Offensive teams leverage CyberOptix’s DevSecOps License to uncover application vulnerabilities with precision, enabling targeted and comprehensive penetration testing.
-
Identify vulnerabilities in applications through SAST, DAST, and repository integrations, focusing on exploitable code. -
Leverage vulnerability data to design more precise and realistic penetration testing strategies. -
Provide detailed insights into exploitable weaknesses to improve code security during development.
How Defensive Teams Use DevSecOps
Defensive teams rely on CyberOptix’s DevSecOps License to seamlessly integrate security into the Software Development Lifecycle (SDLC), ensuring vulnerabilities are identified and mitigated early, before they reach production.
-
Monitor and resolve risks directly within the CI/CD pipeline and source code repositories. -
Seamlessly connect with tools like GitHub and Snyk to address risks as part of the development workflow. -
Focus on high-priority vulnerabilities to reduce the attack surface and ensure secure code deployment.
How Offensive Teams Use Dark Web Monitoring
Offensive teams use CyberOptix’s Dark Web License to simulate real-world attack scenarios, leveraging intelligence gathered from dark web sources.
-
Use intelligence from exposed credentials and breach data to simulate potential threat actor activities. -
Analyze third-party vulnerabilities and executive exposures to uncover new attack vectors. -
Provide insights from simulations that help defensive teams address gaps revealed through dark web intelligence.

Learn More About Dark Web Monitoring
How Defensive Teams Use Dark Web Monitoring
Defensive teams rely on CyberOptix’s Dark Web License to proactively address risks identified on the dark web, such as stolen credentials, vendor breach records, and executive exposure.
-
Identify and reset stolen credentials to prevent unauthorized access. -
Monitor and mitigate risks associated with executive data exposure on the dark web. -
Identify and assess vulnerabilities in vendor breach data to minimize supply chain threats.

Learn More About Dark Web Monitoring
How Offensive Teams Use Dark Web Monitoring
Offensive teams use CyberOptix’s Dark Web License to simulate real-world attack scenarios, leveraging intelligence gathered from dark web sources.
-
Use intelligence from exposed credentials and breach data to simulate potential threat actor activities. -
Analyze third-party vulnerabilities and executive exposures to uncover new attack vectors. -
Provide insights from simulations that help defensive teams address gaps revealed through dark web intelligence.

Learn More About Dark Web Monitoring
How Defensive Teams Use Dark Web Monitoring
Defensive teams rely on CyberOptix’s Dark Web License to proactively address risks identified on the dark web, such as stolen credentials, vendor breach records, and executive exposure.
-
Identify and reset stolen credentials to prevent unauthorized access. -
Monitor and mitigate risks associated with executive data exposure on the dark web. -
Identify and assess vulnerabilities in vendor breach data to minimize supply chain threats.

Learn More About Dark Web Monitoring
Why Use CyberOptix?
The CyberOptix Platform is designed to empower organizations with a unified approach to cybersecurity, providing the tools needed to identify, prioritize, and mitigate risks effectively. Built for modern security challenges, CyberOptix integrates features for offensive and defensive teams, enabling collaboration and ensuring no vulnerability goes unnoticed.
Whether you’re looking to strengthen your defenses, uncover exploitable weaknesses, or streamline vulnerability management, CyberOptix has a solution that can help you.
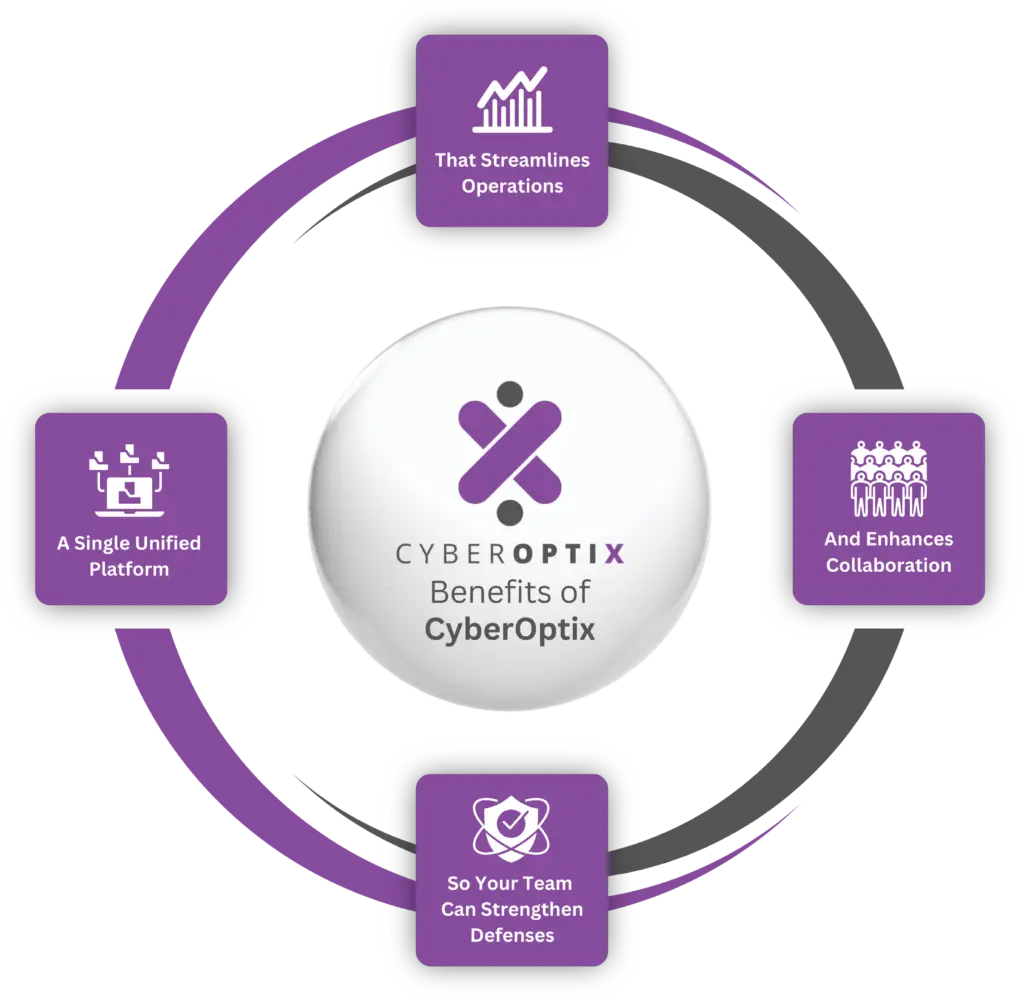
A Single Unified Platform
Bring various cybersecurity tools into one centralized platform, eliminating the need for multiple disconnected systems.
That Streamlines Operations
Simplify workflows and reduce inefficiencies with automated processes and visibility across your environment.
And Enhances Collaboration
Improve collaboration between offensive and defensive security teams to address vulnerabilities more effectively.
So Your Team Can Strengthen Defenses
Proactively identify and remediate threats to fortify your organization’s security posture against ever-evolving cyber risks.
Unify Your Approach to Cybersecurity Operations
CyberOptix unifies your approach to cybersecurity operations by integrating five core solutions into a single, cohesive platform. This eliminates silos and enables your teams to work together efficiently while maintaining full visibility and control over your security landscape.
-
Penetration Testing Management License
Penetration Testing Management License
-
Attack Surface Management License
Attack Surface Management License
-
SIEM License
SIEM License
-
DevSecOps License
DevSecOps License
-
Dark Web License
Dark Web License
Our Articles
Make sure to check out one of our weekly articles, ranging from subjects like purple teaming, to dark web monitoring, and vulnerability management.