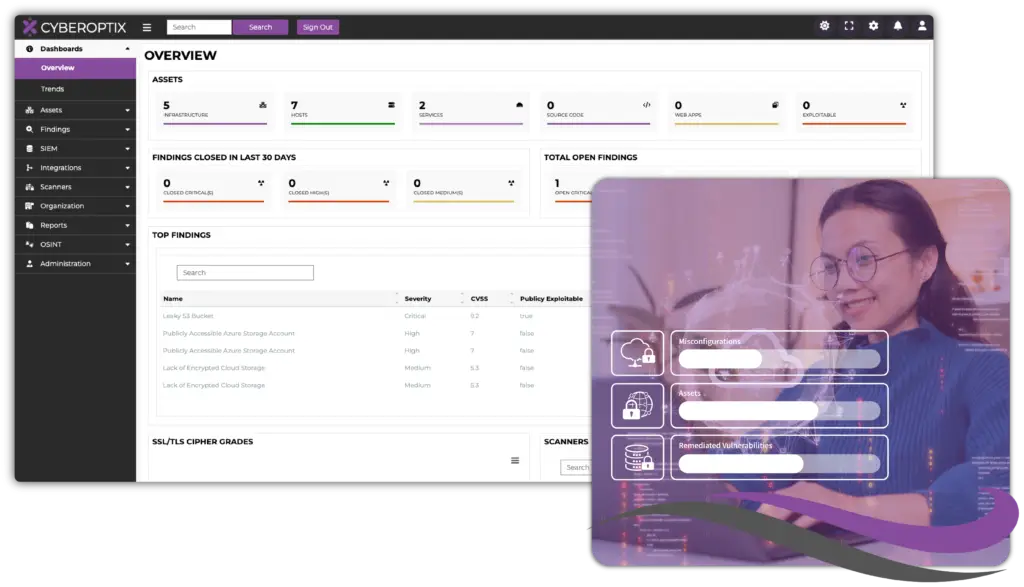
Get Visibility Into Your Entire Attack Surface, Internal, External, and On-Prim.

Traditional Attack Surface Management solutions focus primarily on external cloud environments like AWS, Azure, or Google Cloud, leaving internal assets, hybrid infrastructures, and on-prim systems overlooked. This fragmented approach creates blind spots that attackers can exploit, increasing the risk of breaches.
CyberOptix’s Attack Surface Management (ASM) feature addresses this critical gap. By extending its reach beyond the cloud to include on-premises systems and hybrid environments, our ASM provides a complete and unified view of your organization’s vulnerabilities. Seamlessly integrating with modern enterprise-level systems, it ensures that no part of your infrastructure is left unchecked, empowering your team to identify and mitigate risks proactively.
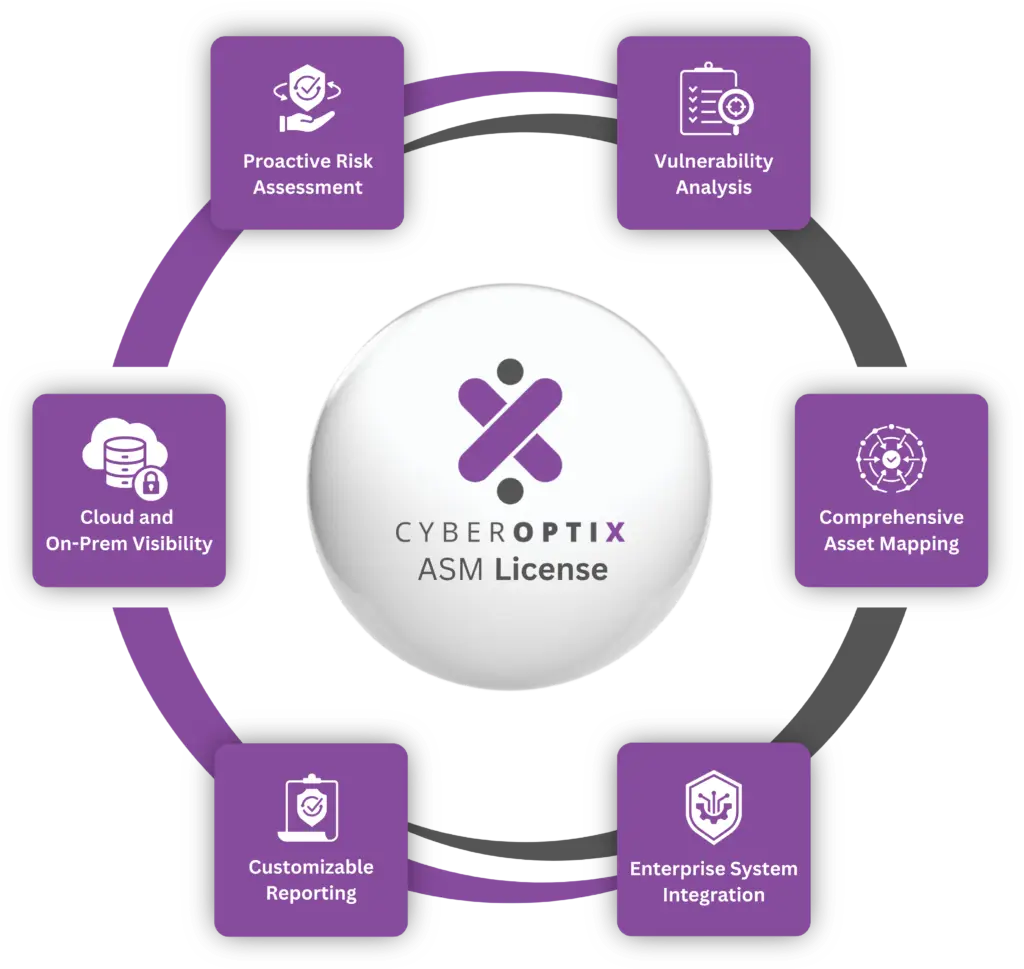
CyberOptix’s Attack Surface Management (ASM) feature provides a robust set of capabilities to help organizations gain full visibility and secure their infrastructure effectively. Unlike traditional solutions, our ASM ensures comprehensive coverage across both cloud and on-premises environments, enabling proactive risk management. Here’s what’s included:
Gain a unified view of your cloud and on-premises environments to ensure no asset is overlooked, enabling full control across hybrid infrastructures.
Anticipate potential threats with continuous risk assessments tailored to your environment, allowing you to address vulnerabilities before they are exploited.
Detect and analyze vulnerabilities across your attack surface with precision, prioritizing threats based on risk factors to focus resources effectively.
Visualize and maintain an up-to-date inventory of all assets within your attack surface, so you can reduce blind spots and strengthen overall security management.
Seamlessly connect CyberOptix with your existing enterprise systems for streamlined workflows and enhanced efficiency from data sharing across platforms.
Generate tailored reports that align with your organization's needs and compliance requirements, allowing you can communicate findings and progress to stakeholders with clear, actionable insights.
Offensive teams use CyberOptix ASM to gain a deeper understanding of both internal and external vulnerabilities, enabling them to conduct more realistic and effective penetration testing. By providing unparalleled visibility into cloud and on-premises environments, ASM equips offensive teams with the insights needed to identify weak points attackers might exploit and simulate advanced threat scenarios.

Analyze vulnerabilities across cloud environments, on-premises systems, and hybrid infrastructures to uncover potential entry points.
Expand the scope and depth of testing, uncovering vulnerabilities across your entire cloud infrastructure including internal, external, and on-prim systems.
Gain detailed insights into cloud infrastructure configurations and practices, identifying exploitable gaps that attackers might target.
Utilize detailed asset mapping and vulnerability data to design precise and impactful attack simulations that mimic real-world scenarios.
Defensive teams rely on CyberOptix ASM to proactively identify, monitor, and remediate vulnerabilities across their entire infrastructure. With visibility into both cloud and on-premises environments, ASM helps defensive teams close security gaps and strengthen their overall posture. This comprehensive approach ensures potential threats are addressed before they can be exploited.

Continuously track newly configured networks, subnets, and internet-connected devices, to maintain full visibility and prevent blind spots.
Address risks across cloud and on-premises systems, ensuring vulnerabilities are remediated before they can be exploited.
Remediate vulnerabilities quickly through instant notifications of significant changes to the attack surface.
Identify and resolve misconfigurations and security gaps in real-time, reducing the risk of breaches and improving your security posture.
Seamlessly integrate ASM with modern enterprise systems to enhance data collection, streamline analysis, and prioritize remediation efforts.
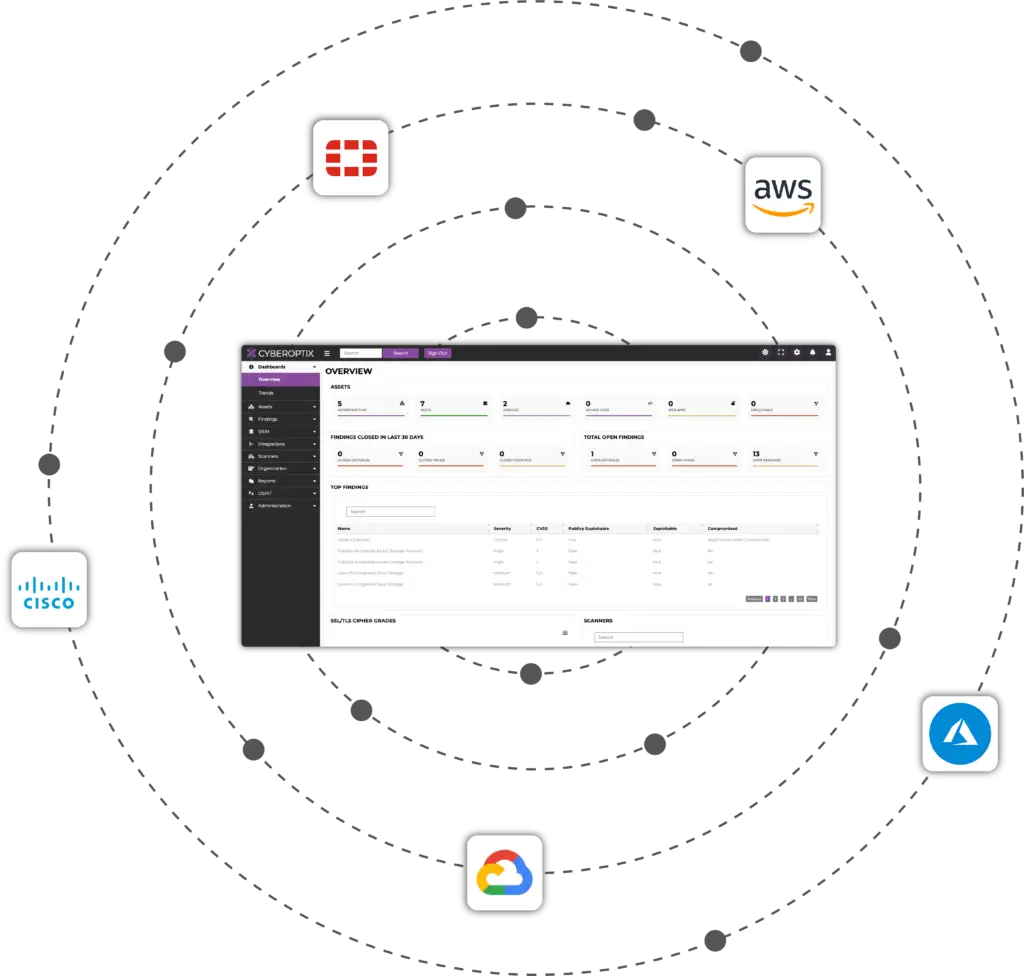
Our Attack Surface Management License integrates seamlessly with leading platforms like Microsoft Azure, AWS, Google Cloud, Cisco, and Fortinet, enabling comprehensive attack surface management. These integrations allow us to unify data from cloud, network, endpoint, and on-premises environments, increasing visibility so your team can mitigate threats.
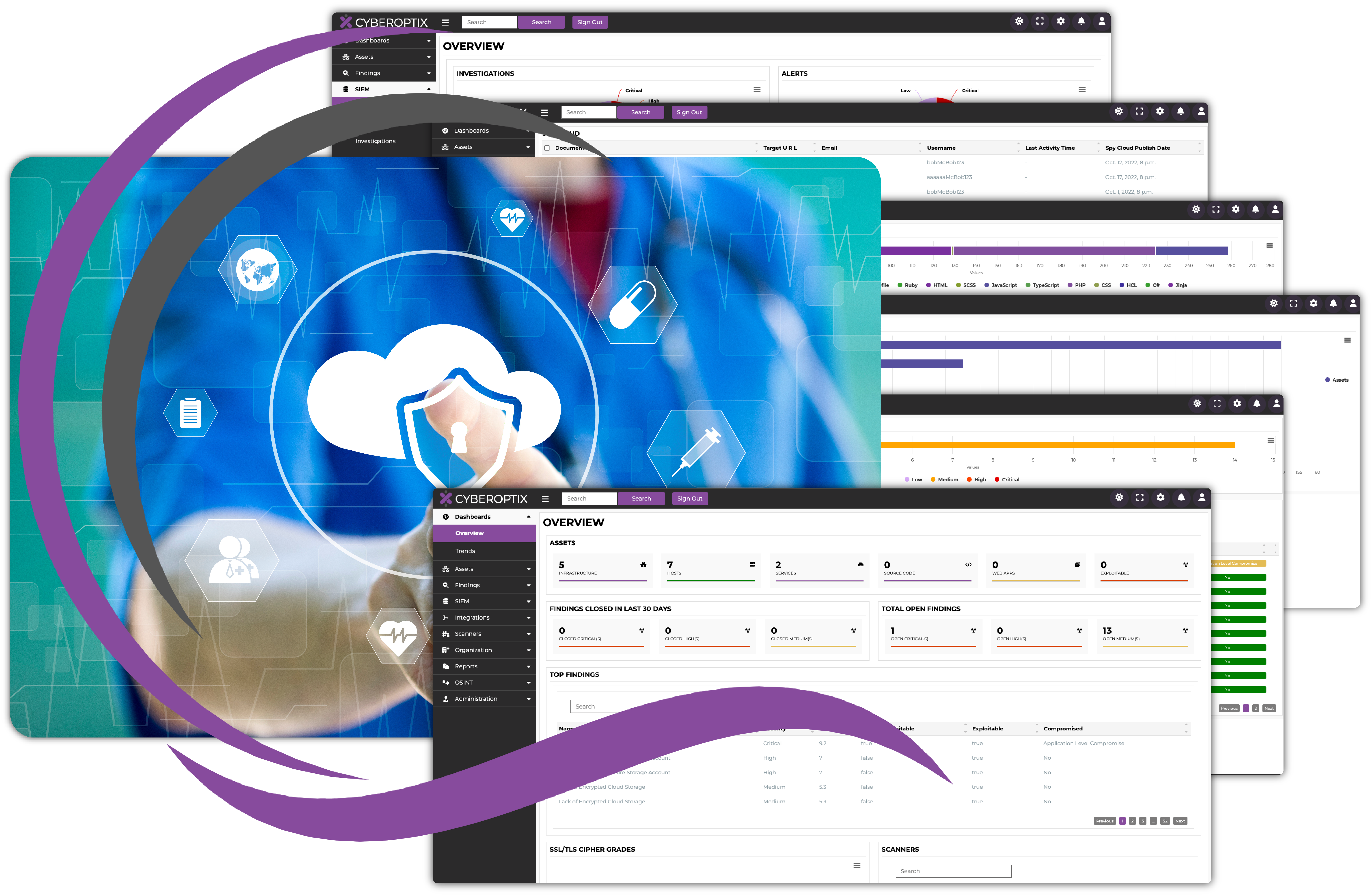
Beyond the capabilities included in the Attack Surface Management License, CyberOptix offers four other licenses that empower organizations to address even more threats and attack vectors from a single place. These features are designed to complement the Attack Surface Management License and provide a deeper level of insight, control, and adaptability.
The Penetration Testing Management License serves as the foundation for offensive security teams to identify vulnerabilities, conduct targeted penetration tests, and refine their strategies.
Defensive teams utilize the Penetration Testing Management License to gain a clear understanding of vulnerabilities within their organization’s infrastructure.
The CyberOptix’s SIEM License empowers offensive teams to conduct advanced simulations and test an organization’s defenses by leveraging real-time insights into logs and security events.
Defensive teams rely on CyberOptix’s SIEM License to gain real-time visibility into security events and logs, enabling them to detect and respond to threats with speed and accuracy.
Offensive teams leverage CyberOptix’s DevSecOps License to uncover application vulnerabilities with precision, enabling targeted and comprehensive penetration testing.
Defensive teams rely on CyberOptix’s DevSecOps License to seamlessly integrate security into the Software Development Lifecycle (SDLC), ensuring vulnerabilities are identified and mitigated early, before they reach production.
Offensive teams use CyberOptix’s Dark Web License to simulate real-world attack scenarios, leveraging intelligence gathered from dark web sources.
Defensive teams rely on CyberOptix’s Dark Web License to proactively address risks identified on the dark web, such as stolen credentials, vendor breach records, and executive exposure.
Don’t let blind spots put your organization at risk. With CyberOptix’s Attack Surface Management License, you gain the comprehensive visibility and actionable insights needed to secure your cloud and on-premises environments.
Contact us today to learn how CyberOptix can redefine your approach to attack surface management and strengthen your organization’s defenses.