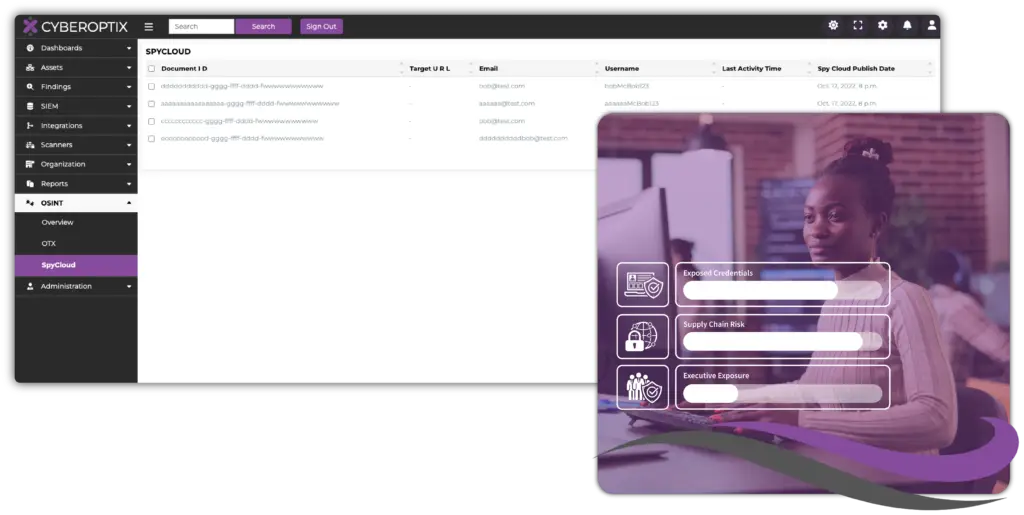
Give Your Security Team Eyes on The Dark Web.

In the hidden corners of the internet, critical information like stolen credentials and sensitive details are often traded or exploited by threat actors. These unseen risks can be used to compromise your organization without warning, leading to data breaches, financial loss, and reputational damage.
The Dark Web Monitoring feature of CyberOptix cuts through the noise, aggregating critical data from the dark web and delivering actionable insights. By identifying your organization’s stolen and compromised credentials, vulnerable vendors, and gauging executive data exposure, this feature equips your team to proactively validate and remediate these risks, strengthening your security posture.
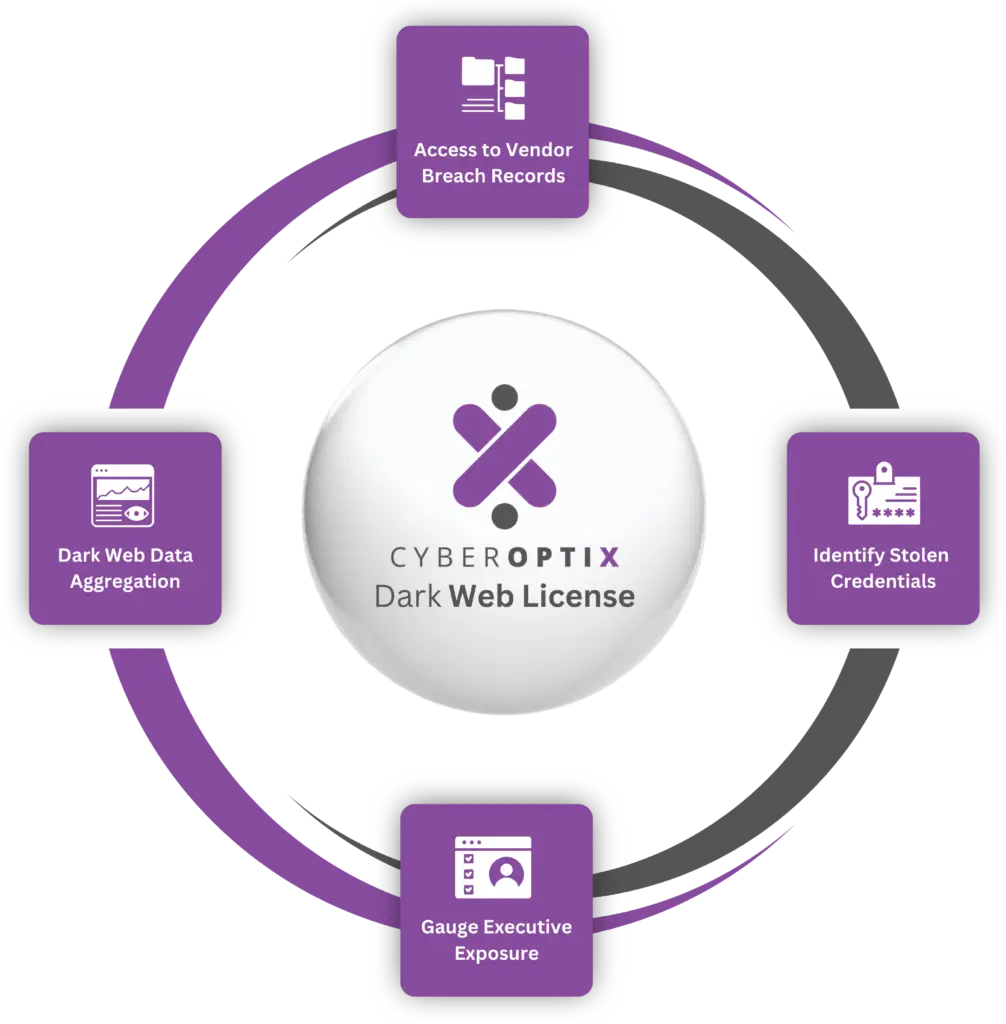
When you purchase the CyberOptix Dark Web Monitoring License, your organization gains access to an advanced monitoring solution designed to uncover and address hidden risks from the dark web. The license includes:
Collect and analyze information from dark web forums, marketplaces, and other sources, so you stay ahead of emerging threats targeting your organization.
Detect when sensitive credentials are leaked on the dark web and act quickly to secure accounts and prevent further exposure.
Monitor for executive-specific data breaches and leaks to prevent targeted attacks, allowing you to protect key personnel and reduce their associated risks to the organization.
Gain insights into vendor-related breaches to mitigate risks in your supply chain, and strengthen partnerships by holding vendors accountable for their security practices.

Offensive security teams can use the CyberOptix Dark Web Monitoring feature to simulate real-world attack scenarios and test the resilience of the organization’s defenses. By incorporating dark web insights into their penetration testing and attack simulations, offensive teams can better evaluate the organization’s defenses and provide actionable recommendations to strengthen them.

Test organizational defenses using real compromised credentials sourced from the dark web.
Use dark web intelligence to design more accurate penetration tests that mimic threat actor tactics.
Ensure previous vulnerabilities have been resolved by using dark web intelligence.
Assess third-party vendor breach records to uncover weak links in the supply chain.
Defensive security teams utilize the insights from Dark Web Monitoring to proactively address risks and fortify the organization’s security posture. With real-time visibility into exposed data, such as compromised credentials and third-party vulnerabilities, defenders can prioritize and remediate risks effectively. This feature enables teams to stay ahead of emerging threats and protect critical assets.

Identify and reset compromised credentials to prevent unauthorized access.
Monitor and safeguard executive information to mitigate risks of targeted attacks.
Track vendor exposures to ensure third-party partners don't put your organization at risk.
The CyberOptix Dark Web Monitoring License integrates seamlessly with leading platforms like CrowdStrike, SpyCloud, and Recorded Future. These integrations enhance the detection and monitoring of exposed credentials, compromised assets, and sensitive information across the dark web.



Beyond the capabilities included in the Dark Web License, CyberOptix offers four other licenses that empower organizations to address even more threats and attack vectors from a single place. These features are designed to complement the Dark Web License and provide a deeper level of insight, control, and adaptability.
The Penetration Testing Management License serves as the foundation for offensive security teams to identify vulnerabilities, conduct targeted penetration tests, and refine their strategies.
Defensive teams utilize the Penetration Testing Management License to gain a clear understanding of vulnerabilities within their organization’s infrastructure.
CyberOptix’s Attack Surface Management License provides offensive teams with visibility into both internal and external vulnerabilities, allowing them to craft realistic attack scenarios.
Defensive teams use CyberOptix’s Attack Surface Management License to gain a comprehensive view of their attack surface, enabling them to identify and close security gaps proactively.
The CyberOptix’s SIEM License empowers offensive teams to conduct advanced simulations and test an organization’s defenses by leveraging real-time insights into logs and security events.
Defensive teams rely on CyberOptix’s SIEM License to gain real-time visibility into security events and logs, enabling them to detect and respond to threats with speed and accuracy.
Offensive teams leverage CyberOptix’s DevSecOps License to uncover application vulnerabilities with precision, enabling targeted and comprehensive penetration testing.
Defensive teams rely on CyberOptix’s DevSecOps License to seamlessly integrate security into the Software Development Lifecycle (SDLC), ensuring vulnerabilities are identified and mitigated early, before they reach production.
Take control of your cybersecurity strategy with the CyberOptix’s Dark Web License. Whether you’re defending your organization against supply chain attacks or using stolen credentials in your testing, this feature provides the information your team needs to secure your organization.
Equip your team with the tools to identify vulnerabilities, remediate risks, and protect what matters most. Contact us today to learn more and get started.