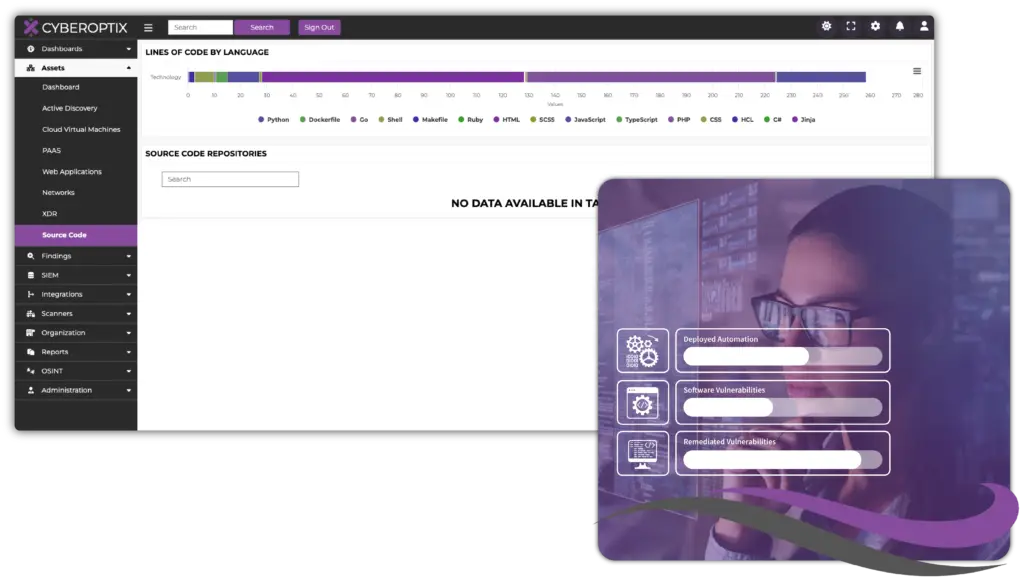
Integrate Security Seamlessly Into Your Software Development Life Cycle (SDLC).

Many organizations use disjointed tools and siloed processes leaving critical vulnerabilities unnoticed, exposing organizations to significant risk. Security teams often lack the visibility needed to monitor applications effectively, while developers struggle to integrate security seamlessly into their workflows.
The CyberOptix DevSecOps License solves these challenges by uniting your tools and pipelines under a single platform. With integrations for SAST tools, DAST within CI/CD pipelines, and Git repositories, your teams gain complete visibility into application vulnerabilities, breaking down barriers between development and security. This approach empowers your organization to build secure applications without slowing innovation.
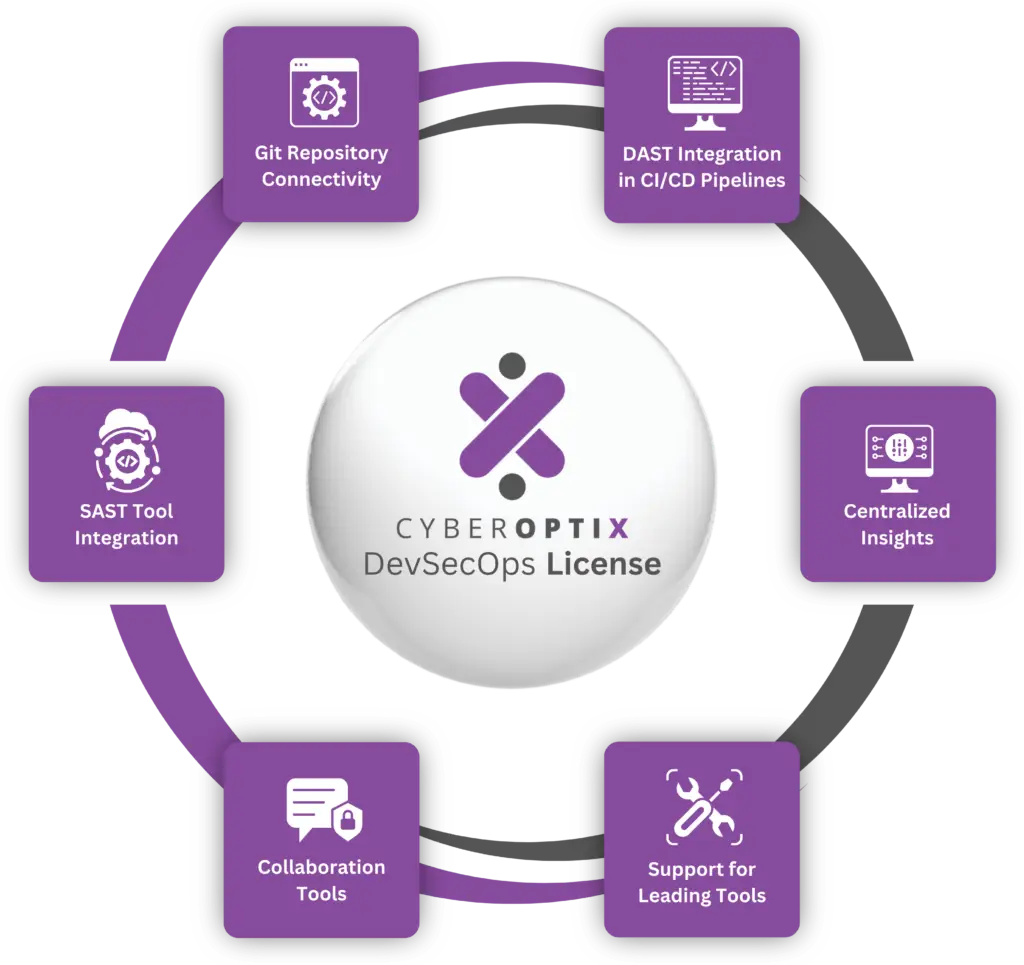
When you purchase the CyberOptix DevSecOps License, your organization gains access to a suite of features designed to integrate security seamlessly into your development pipeline and provide visibility into application vulnerabilities. The license includes:
Integrate static analysis tools to identify vulnerabilities in your codebase, allowing you to detect issues early in the development lifecycle, reducing remediation costs.
Monitor and scan Git repositories for sensitive data leaks or vulnerabilities, allowing you to protect your codebase from misconfigurations and unauthorized access.
Perform dynamic scans on running applications to find vulnerabilities missed during static analysis, enhancing security with a dual-layered approach to testing.
Aggregate vulnerability data into a single dashboard for easy tracking and management, giving you a holistic view of your security posture.
Connect with industry-standard tools to maximize efficiency and compatibility, allowing you to consolidate and build on your existing toolset while strengthening your security framework.
Enable seamless teamwork with tools for task assignment, communication, and progress tracking, making sure all stakeholders are aligned on goals and responsibilities.
Offensive teams use the CyberOptix DevSecOps License to gain a deeper understanding of application vulnerabilities, enabling more effective and targeted testing. By accessing real-time data from integrated tools and repositories, offensive teams can replicate real-world attack scenarios, uncover hidden weaknesses, and ensure that security defenses are thoroughly evaluated.
Access in-depth insights about applications being tested through a centralized platform.
Ensure comprehensive testing by leveraging data from integrated DAST and SAST tools, and GitHub repositories.
Leverage centralized intelligence to streamline the remediation of vulnerabilities that would go unnoticed.
Defensive teams rely on the CyberOptix DevSecOps License to integrate security into the development lifecycle, addressing risks proactively and ensuring a secure application pipeline. By connecting with critical tools and systems, defensive teams can identify vulnerabilities early, monitor risks in real-time, and collaborate more effectively with developers.

Seamlessly connect with GitHub, GitLab, Bitbucket, and Snyk to monitor vulnerabilities across repositories.
Detect and remediate issues early in the development lifecycle to reduce risks before deployment.
Improve coordination between development and security by sharing insights and centralizing reporting.
Ensure dynamic security testing is embedded within the pipeline to catch risks in real-time.
The CyberOptix DevSecOps License seamlessly connects with critical development and security platforms, including GitHub, GitLab, Bitbucket, Jenkins, Red Hat, and Snyk. These integrations provide end-to-end visibility and control over your software development lifecycle, ensuring security is embedded from code to deployment.






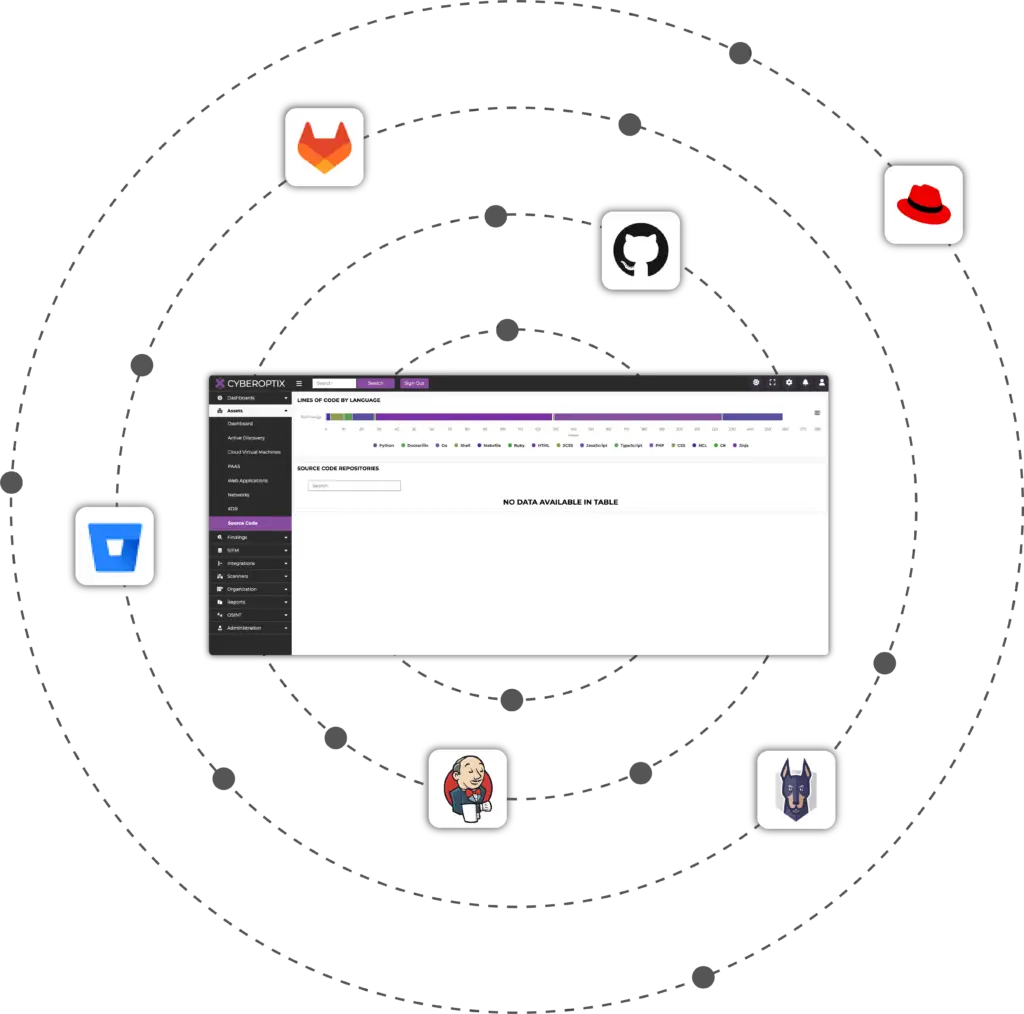
Beyond the capabilities included in the DevSecOps License, CyberOptix offers four other licenses that empower organizations to address even more threats and attack vectors from a single place. These features are designed to complement the DevSecOps License and provide a deeper level of insight, control, and adaptability.
The Penetration Testing Management License serves as the foundation for offensive security teams to identify vulnerabilities, conduct targeted penetration tests, and refine their strategies.
Defensive teams utilize the Penetration Testing Management License to gain a clear understanding of vulnerabilities within their organization’s infrastructure.
CyberOptix’s Attack Surface Management License provides offensive teams with visibility into both internal and external vulnerabilities, allowing them to craft realistic attack scenarios.
Defensive teams use CyberOptix’s Attack Surface Management License to gain a comprehensive view of their attack surface, enabling them to identify and close security gaps proactively.
Offensive teams leverage CyberOptix’s DevSecOps License to uncover application vulnerabilities with precision, enabling targeted and comprehensive penetration testing.
Defensive teams rely on CyberOptix’s DevSecOps License to seamlessly integrate security into the Software Development Lifecycle (SDLC), ensuring vulnerabilities are identified and mitigated early, before they reach production.
Offensive teams use CyberOptix’s Dark Web License to simulate real-world attack scenarios, leveraging intelligence gathered from dark web sources.
Defensive teams rely on CyberOptix’s Dark Web License to proactively address risks identified on the dark web, such as stolen credentials, vendor breach records, and executive exposure.
Don’t let vulnerabilities slip through the cracks during development. CyberOptix’s DevSecOps License empowers your team to integrate security seamlessly into the software development lifecycle, ensuring risks are identified and mitigated before deployment.
Contact us today to see how CyberOptix DevSecOps can transform your approach to application security.