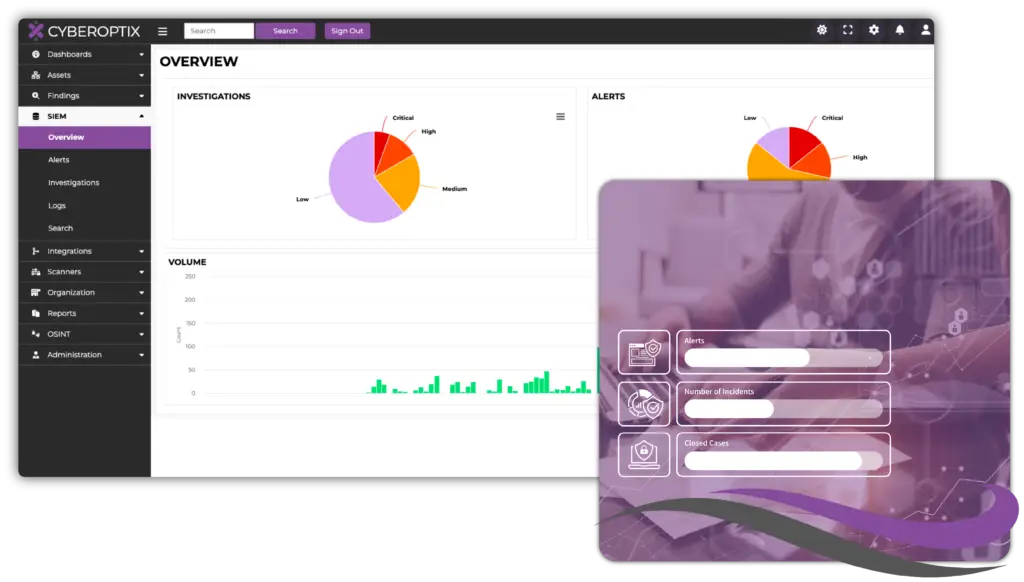
Enhancing Collaboration Between Offensive and Defensive Security Teams.

You’re probably wondering “Why do we need another SIEM solution?”, a fair question considering the multitude of options. The reality is that many traditional SIEM tools fail to foster collaboration between red and blue teams.
This disconnect results in a significant opportunity cost: organizations miss out on the full potential of purple teaming, where offensive and defensive teams come together to simulate attacks, fine-tune defenses, and proactively identify vulnerabilities. Without this synergy, defenses remain reactive, leaving critical gaps unaddressed.
The CyberOptix SIEM License changes the game by integrating purple teaming into its core functionality. This isn’t just a SIEM—it’s a platform for collaboration, enabling red and blue teams to work together through real-time attack simulations, enhancing threat detection, and strengthening defensive strategies.
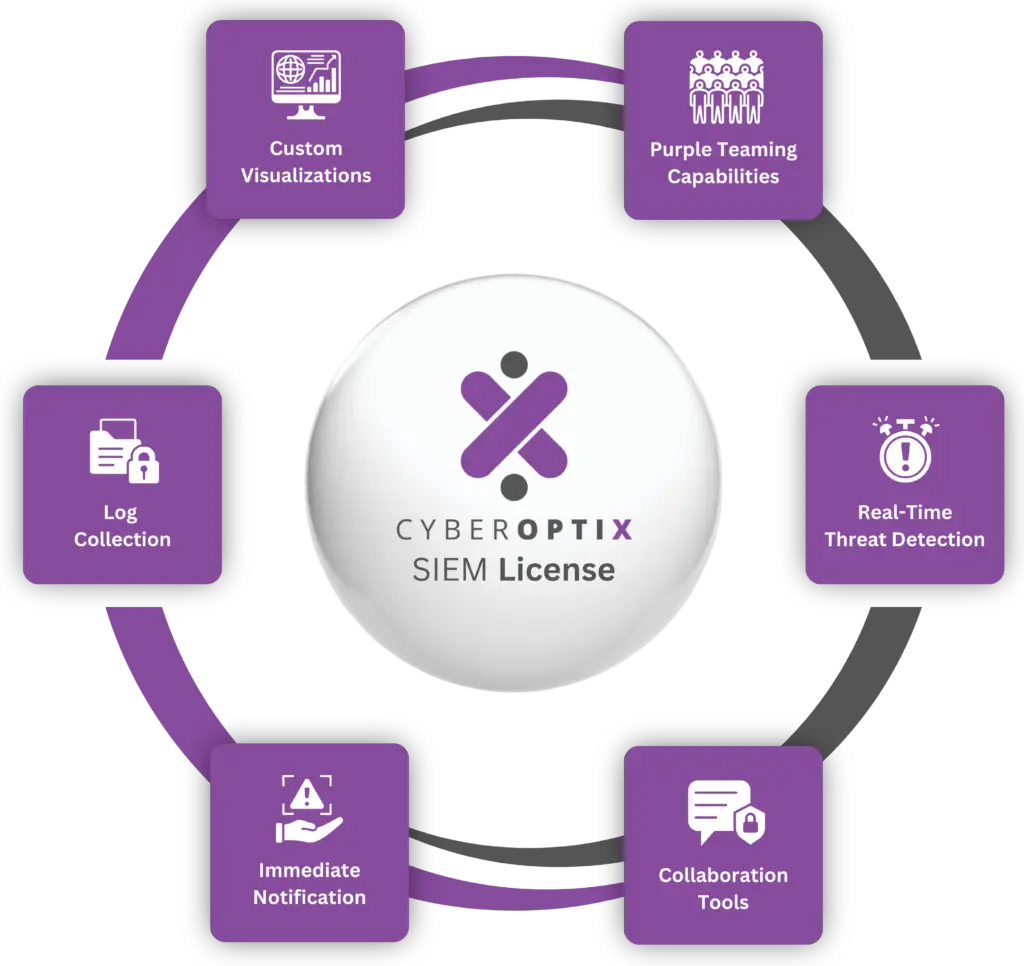
When you choose the CyberOptix SIEM License, you’re not just investing in a tool—you’re enabling a collaborative, purple-teaming approach to cybersecurity. Here’s what’s included:
Collect and index log data from diverse sources for centralized analysis, ensuring quick access to insights that keep your organization secure.
Create tailored dashboards to highlight critical metrics and insights. Adapt visualizations to fit your organization’s unique needs and goals.
Simulate and defend against attacks in a collaborative environment, strengthening your defenses by combining offensive and defensive strategies.
Detect and respond to threats as they occur with instant notifications, minimizing response times to mitigate potential damage.
Facilitate teamwork with features designed to enhance communication and task sharing, keeping teams aligned and efficient, even during high-pressure situations.
Receive alerts about threats or unusual activities in real time, keeping your team informed and ready to act at a moment’s notice.
Offensive teams use the CyberOptix SIEM to simulate realistic attack scenarios and test the visibility of their activities within the organization’s defenses. By leveraging the platform’s real-time log data and proprietary correlation tools, offensive teams can refine their techniques to replicate adversarial behavior and identify weaknesses that could be exploited. This collaboration with defensive teams through purple teaming ensures a more comprehensive understanding of vulnerabilities and defenses.

Analyze how “loud” simulated attacks appear in log data, helping you to refine tactics and techniques.
Conduct controlled attack simulations to evaluate the organization’s defenses and uncover exploitable gaps.
Work alongside defenders in purple teaming exercises to enhance the overall security posture through collaboration.
Defensive teams rely on CyberOptix SIEM to gain real-time insights into security events, enabling them to detect and respond to potential breaches with precision. The platform’s proprietary correlations and visualizations allow defenders to analyze attacker behavior, prioritize threats, and mitigate risks effectively. Through purple teaming, defensive teams collaborate with offensive teams to refine detection capabilities and close gaps in their defenses.

Leverage advanced correlations and visualizations to detect and respond to suspicious activities immediately.
Work alongside offensive teams during simulations to analyze and strengthen defensive measures in real time.
Identify vulnerabilities exposed during simulations or active events and implement fixes before attackers exploit them.
Gain actionable insights into attack origins, techniques, and targets to better understand threats.
The CyberOptix SIEM License integrates seamlessly with industry-leading platforms such as Microsoft Defender, Bitdefender, and CrowdStrike. These integrations unify security data across endpoints, networks, and cloud environments, delivering immediate notification of potential breaches in security.





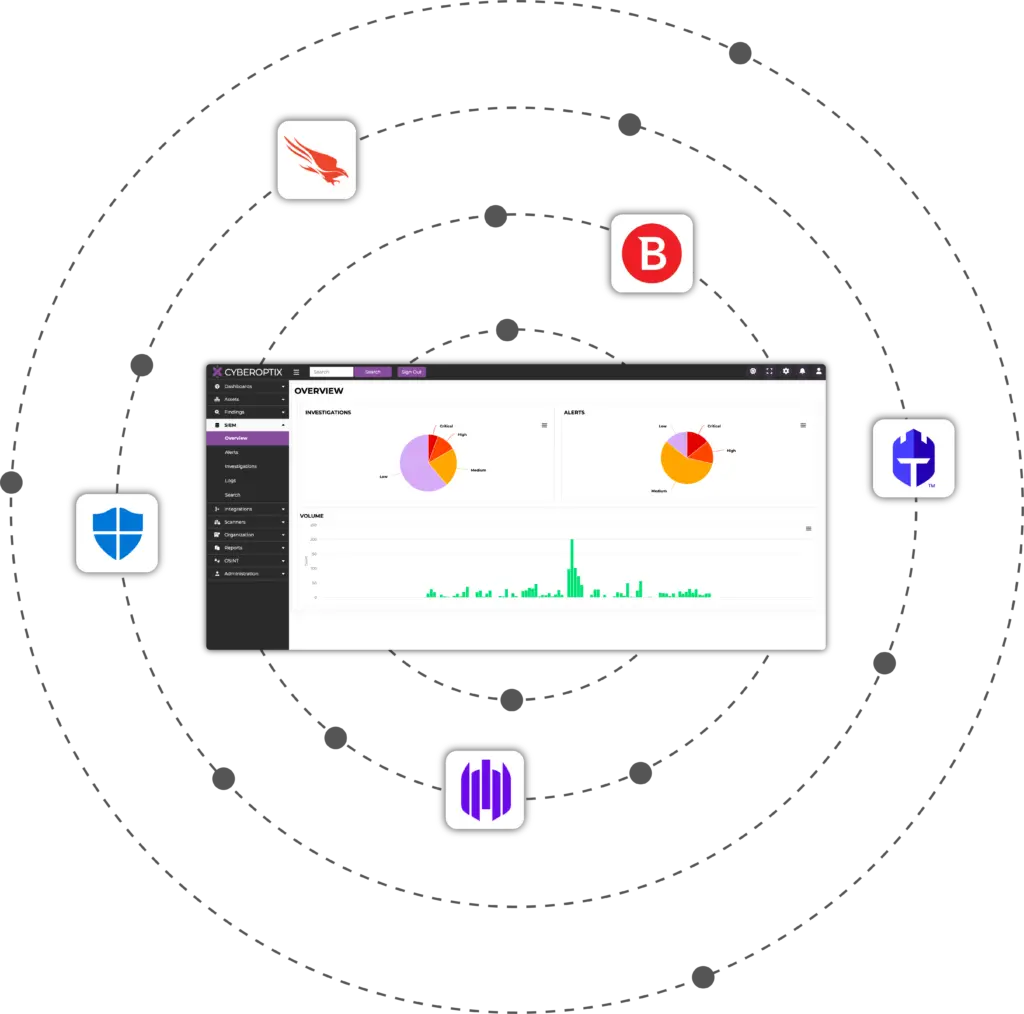
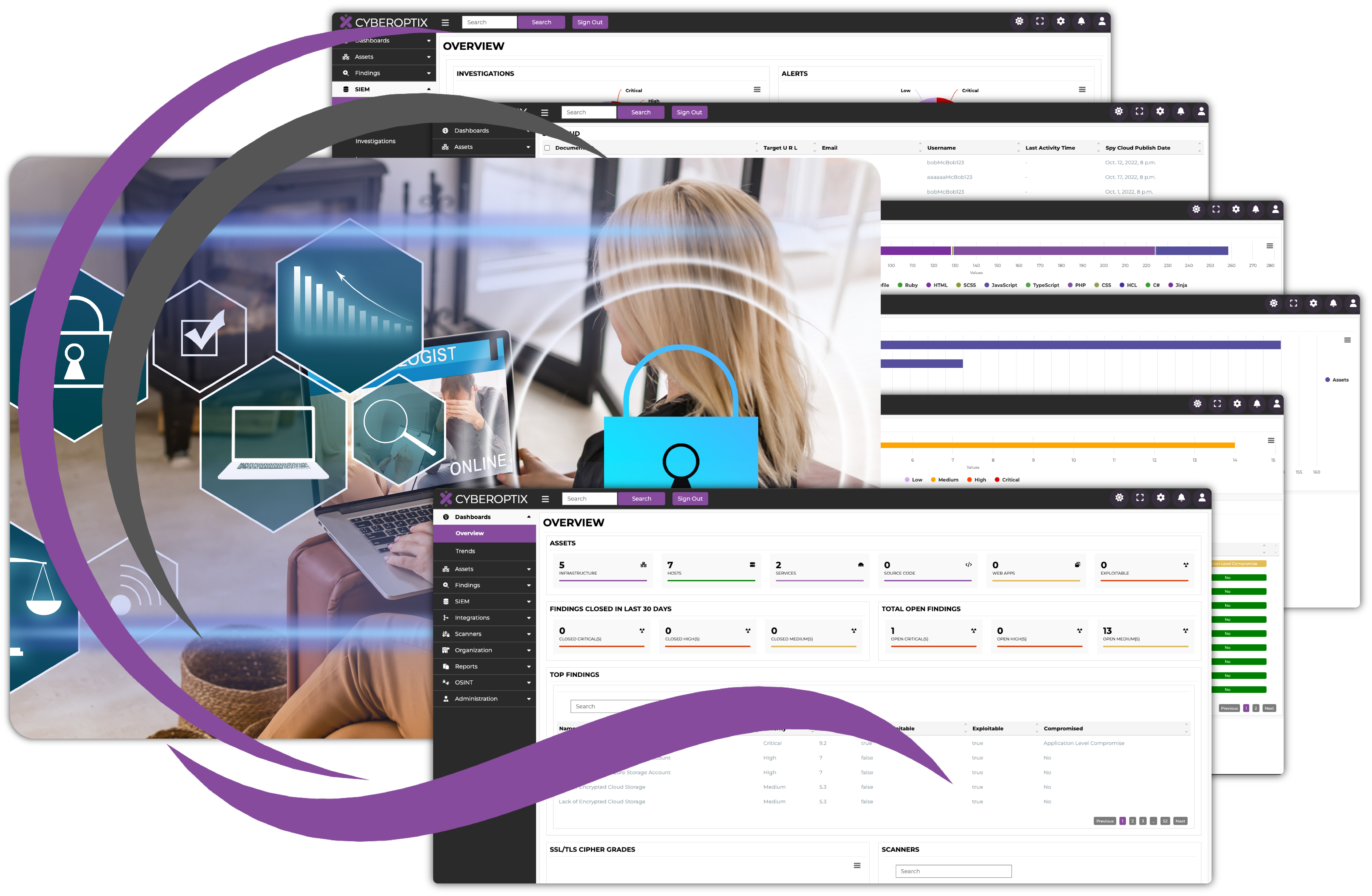
Beyond the capabilities included in the SIEM License, CyberOptix offers four other licenses that empower organizations to address even more threats and attack vectors from a single place. These features are designed to complement the SIEM License and provide a deeper level of insight, control, and adaptability.
The Penetration Testing Management License serves as the foundation for offensive security teams to identify vulnerabilities, conduct targeted penetration tests, and refine their strategies.
Defensive teams utilize the Penetration Testing Management License to gain a clear understanding of vulnerabilities within their organization’s infrastructure.
CyberOptix’s Attack Surface Management License provides offensive teams with visibility into both internal and external vulnerabilities, allowing them to craft realistic attack scenarios.
Defensive teams use CyberOptix’s Attack Surface Management License to gain a comprehensive view of their attack surface, enabling them to identify and close security gaps proactively.
Offensive teams leverage CyberOptix’s DevSecOps License to uncover application vulnerabilities with precision, enabling targeted and comprehensive penetration testing.
Defensive teams rely on CyberOptix’s DevSecOps License to seamlessly integrate security into the Software Development Lifecycle (SDLC), ensuring vulnerabilities are identified and mitigated early, before they reach production.
Offensive teams use CyberOptix’s Dark Web License to simulate real-world attack scenarios, leveraging intelligence gathered from dark web sources.
Defensive teams rely on CyberOptix’s Dark Web License to proactively address risks identified on the dark web, such as stolen credentials, vendor breach records, and executive exposure.
Don’t settle for a traditional SIEM that keeps your teams working in silos. CyberOptix’s SIEM License empowers your organization with real-time insights, advanced analytics, and the collaborative power of purple teaming.
Strengthen your defenses, refine your strategies, and stay ahead of threats with a solution designed to unify and elevate your security operations. Contact us today to learn how CyberOptix SIEM can transform the way your teams protect your organization.