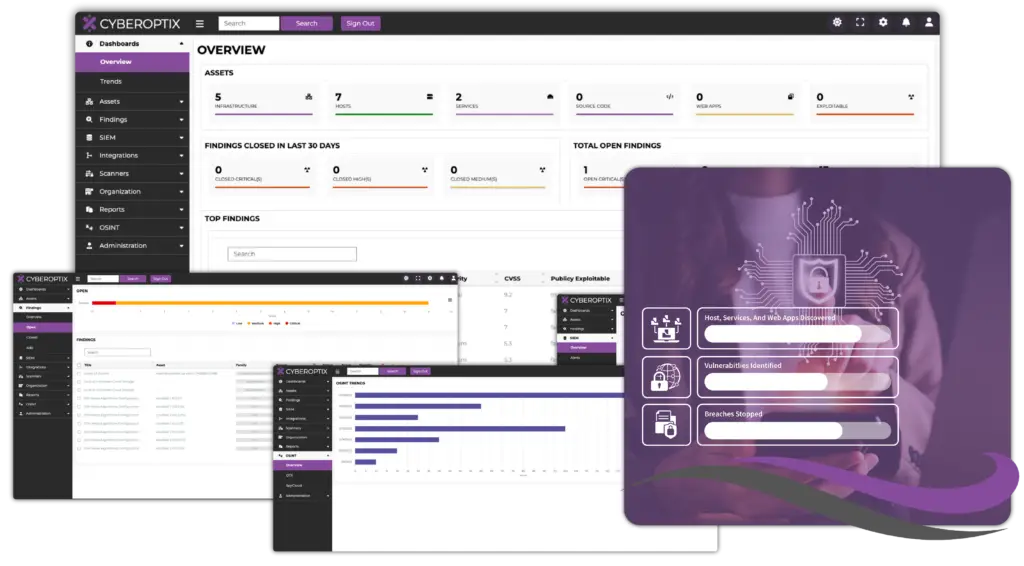
Streamline Cybersecurity Operations and Enhance Collaboration With CyberOptix.

Managing vulnerability identification and remediation in today’s fast-paced environment is harder than ever. Your security team is juggling dozens of fragmented security tools and struggling to collaborate effectively, resulting in a missed opportunity to remediate vulnerabilities more efficiently.
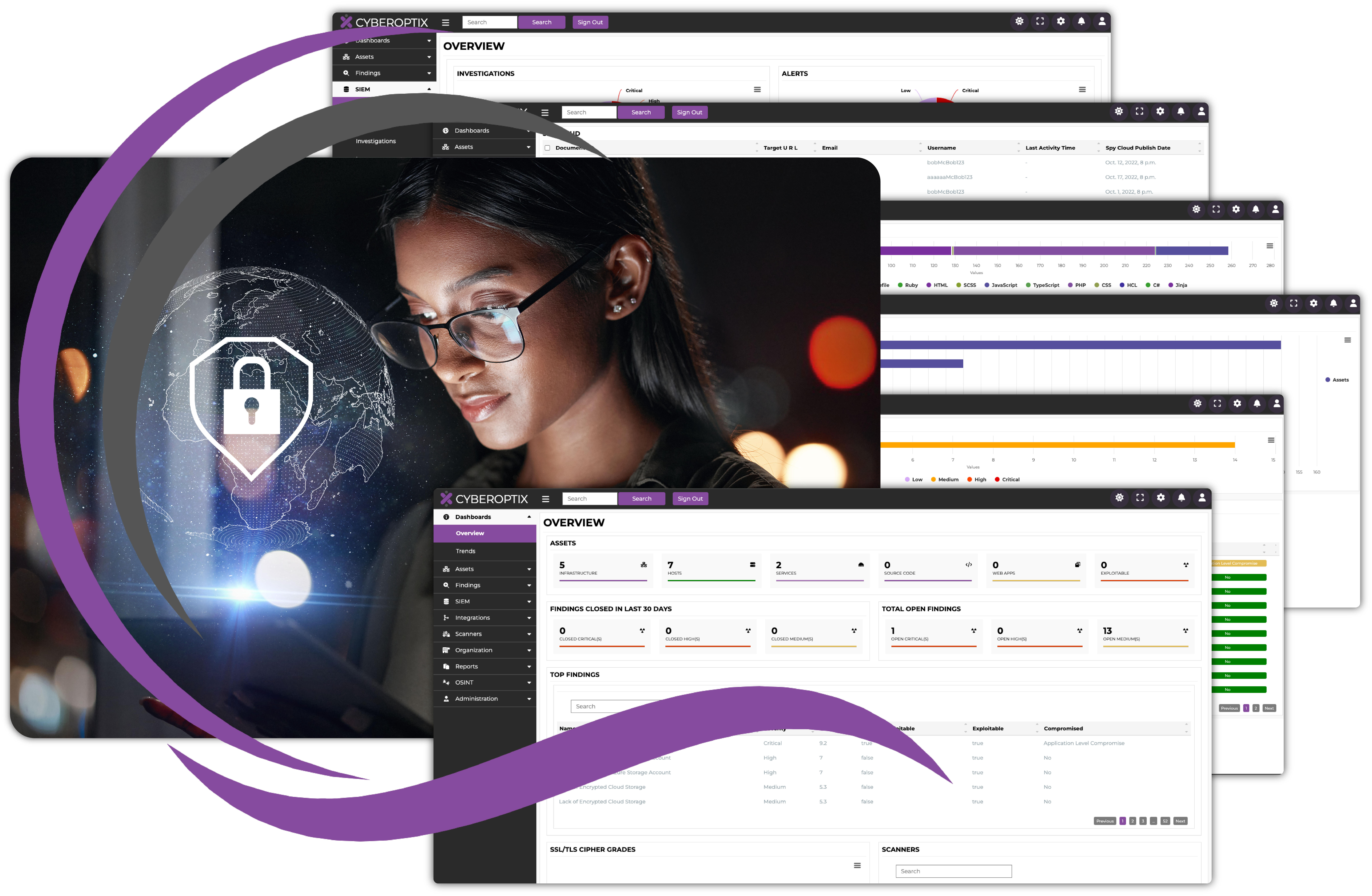
CyberOptix understands these challenges and was designed to address these problems. Our platform brings together essential cybersecurity tools like vulnerability scanning, risk analysis, open source intelligence, Attack Surface Management, SIEM, DevSecOps, Dark Web Monitoring, and more into a single, unified interface, giving your team the visibility, efficiency, and collaboration they need to succeed. CyberOptix helps you take control of your security strategy and stay ahead of threats, empowering your organization to proactively identify and address vulnerabilities.
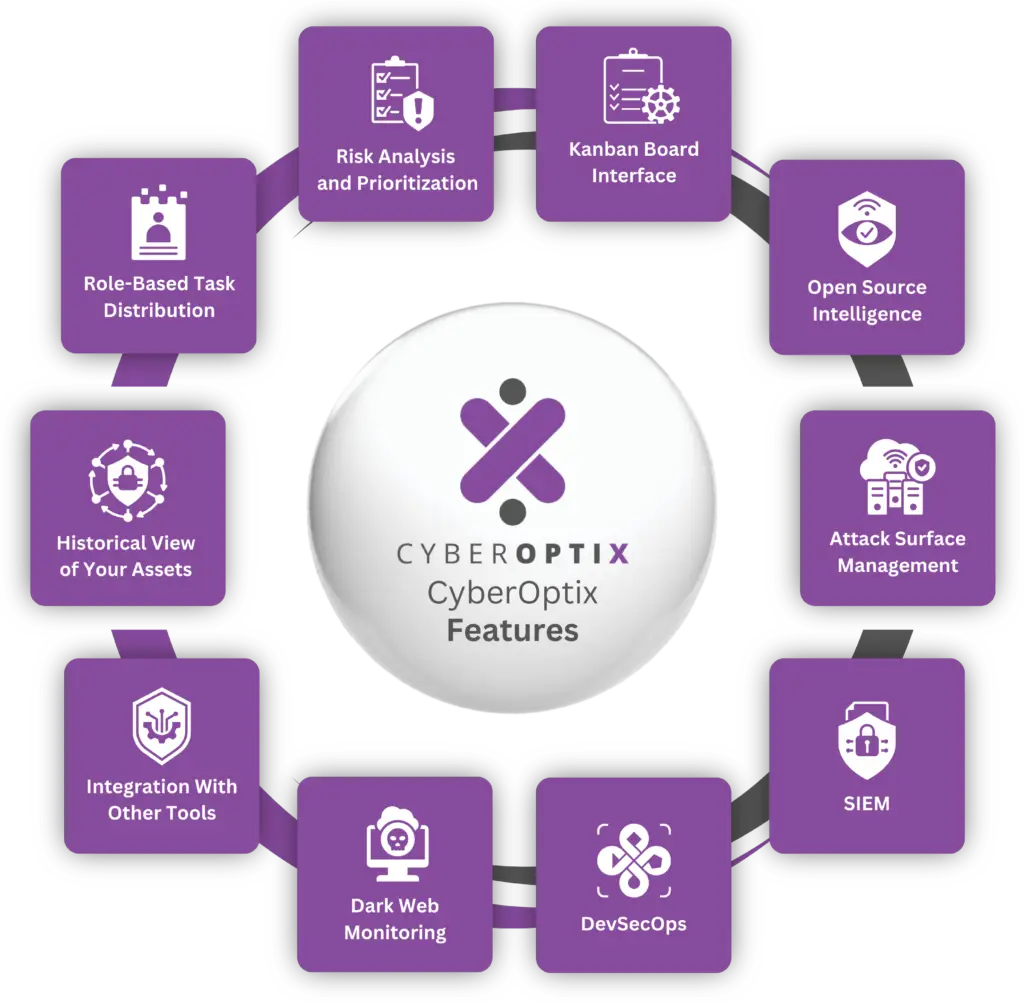
The CyberOptix platform is home to a comprehensive suite of capabilities designed to streamline cybersecurity operations. Key features include:
CyberOptix allows you to access past versions of your assets, complete with a detailed snapshot of all vulnerabilities present at that specific point in time.
Assign tasks to specific team members based on their role, optimizing productivity and streamlining vulnerability remediation.
Automatically categorize and prioritize vulnerabilities based on risk level, allowing your team to focus on resolving the most pressing issues.
Organize tasks and track remediation progress visually on our kanban board interface, improving team collaboration and streamlining workflows.
Integrate with OSINT tools to consolidate publicly available information into one platform, enhancing your understanding of threats.
Map and monitor your organization’s internal, external, and on-prim assets from just one location, so you can stay ahead of attackers by reducing your attack surface in real time.
Go beyond just monitoring and responding to threats in real time with our platform's focus on enhancing collaboration between red and blue teams, so you can reap the benefits of purple teaming.
Integrate security into your development processes by seamless integrating with DAST, SAST, Git Repositories, and other security tools for faster, safer software releases.
Proactively safeguard your organization from emerging threats by detecting and addressing exposed credentials, gauging executive data exposure, and monitoring vendor breach records.
Seamlessly connect CyberOptix with other security tools for a unified approach. Enhance your existing workflows and maximize efficiency.
Offensive teams leverage CyberOptix to uncover vulnerabilities and simulate realistic attack scenarios, giving them the tools and insights needed to test the strength of an organization’s defenses. By providing detailed visibility into internal and external risks, the platform allows offensive teams to refine their methodologies, identify exploitable gaps, and provide actionable data to improve overall security strategies.

Use vulnerability insights from Attack Surface Management and Dark Web Monitoring to craft realistic attack scenarios.
Gain a comprehensive view of vulnerabilities to expand testing coverage and precision.
Analyze how security practices in cloud environments and internal systems can be exploited by attackers.
Deliver detailed findings to defensive teams to help enhance their mitigation strategies.
Defensive teams rely on CyberOptix to proactively monitor risks, close gaps, and strengthen their organization’s defenses. By integrating real-time insights with a kanban board interface to track remediation, and role based task distribution, our platform empowers defensive teams to respond effectively to threats and embed security into every layer of the organization’s infrastructure.

Track vulnerabilities across cloud, on-premises, and hybrid environments with a kanban board interface.
Identify over 20 different types of vulnerabilities in your networks, systems and applications.
Integrate with DevSecOps workflows to address risks early in the development lifecycle.
Use centralized data and analysis to quickly detect and neutralize threats across all your assets.
Distribute task to your security team based on their role, streamlining and simplifying the remediation process.
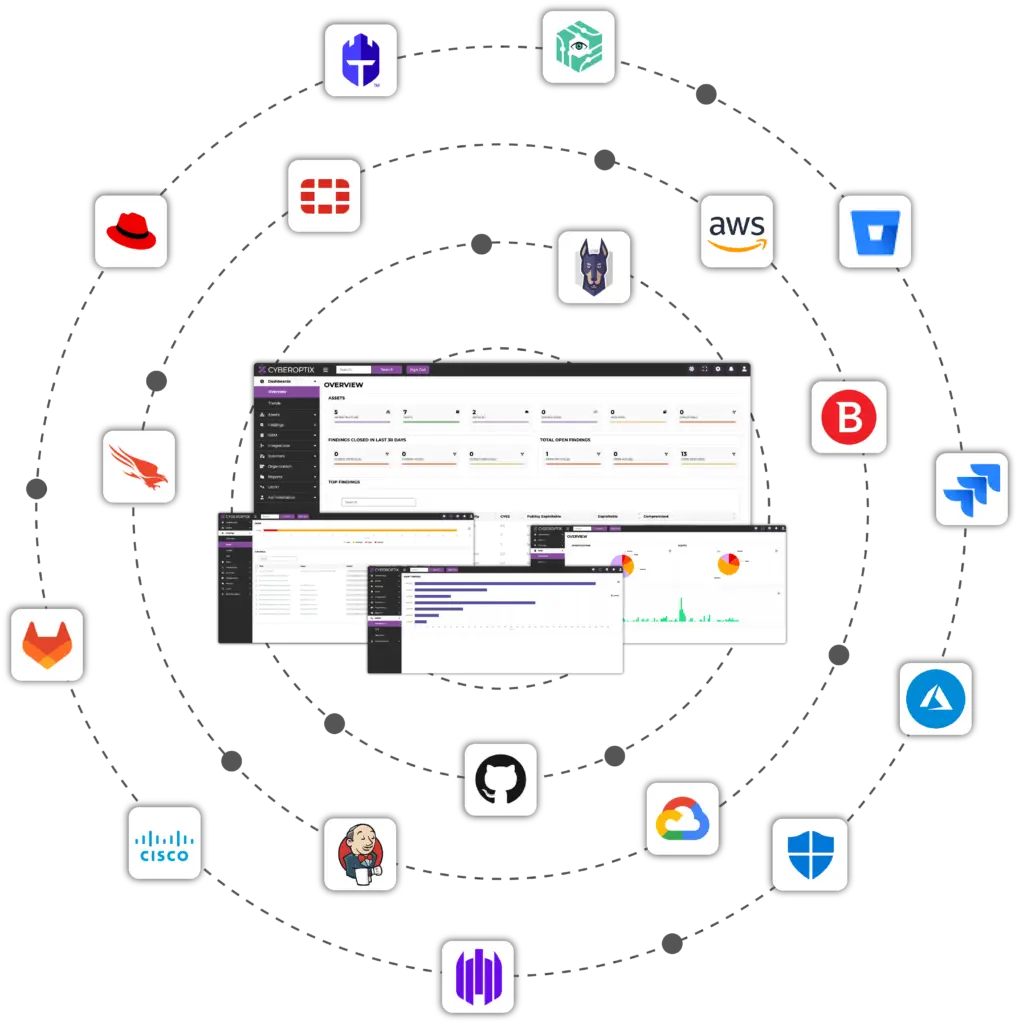
The CyberOptix platform integrates with a wide range of leading tools and technologies, including Microsoft Azure, AWS, Google Cloud, GitHub, GitLab, Bitbucket, Jenkins, Red Hat, Snyk, Cisco, Fortinet, CrowdStrike, Microsoft Defender, Bitdefender, and more. These integrations provide a cohesive ecosystem for managing cybersecurity across development, cloud, endpoint, network, and on-premises environments.
By consolidating data and automating processes, CyberOptix empowers security teams to collaboratively address a wide variety of threats and vulnerabilities from one platform.


















The CyberOptix Platform offers five distinct licenses, all of which are designed to bridge the gap between offensive and defensive teams, helping them to collaboratively identify and remediate vulnerabilities.
Each license addresses a specific set of threats, and provides your security team with a unique set of tools to address them.
Wether you struggle with remediating dark web threats, securing your software, or reducing vulnerabilities in your cloud infrastructure, we have a license that can help you.
The Penetration Testing Management License serves as the foundation for offensive security teams to identify vulnerabilities, conduct targeted penetration tests, and refine their strategies.
Defensive teams utilize the Penetration Testing Management License to gain a clear understanding of vulnerabilities within their organization’s infrastructure.
CyberOptix’s Attack Surface Management License provides offensive teams with visibility into both internal and external vulnerabilities, allowing them to craft realistic attack scenarios.
CyberOptix’s Attack Surface Management License provides offensive teams with visibility into both internal and external vulnerabilities, allowing them to craft realistic attack scenarios.
The CyberOptix’s SIEM License empowers offensive teams to conduct advanced simulations and test an organization’s defenses by leveraging real-time insights into logs and security events.
Defensive teams rely on CyberOptix’s SIEM License to gain real-time visibility into security events and logs, enabling them to detect and respond to threats with speed and accuracy.
Offensive teams leverage CyberOptix’s DevSecOps License to uncover application vulnerabilities with precision, enabling targeted and comprehensive penetration testing.
Defensive teams rely on CyberOptix’s DevSecOps License to seamlessly integrate security into the Software Development Lifecycle (SDLC), ensuring vulnerabilities are identified and mitigated early, before they reach production.
Offensive teams use CyberOptix’s Dark Web License to simulate real-world attack scenarios, leveraging intelligence gathered from dark web sources.
Defensive teams rely on CyberOptix’s Dark Web License to proactively address risks identified on the dark web, such as stolen credentials, vendor breach records, and executive exposure.
CyberOptix isn’t just another security tool—it’s your all-in-one platform for managing vulnerabilities, enhancing collaboration, and proactively addressing cyber risks. With its combination of five core solutions into one platform, CyberOptix empowers your team to collaboratively address threats from a single platform, safeguarding your organization’s most critical assets.
Contact us now to schedule a demo and discover how CyberOptix can revolutionize your organization’s approach to cybersecurity.