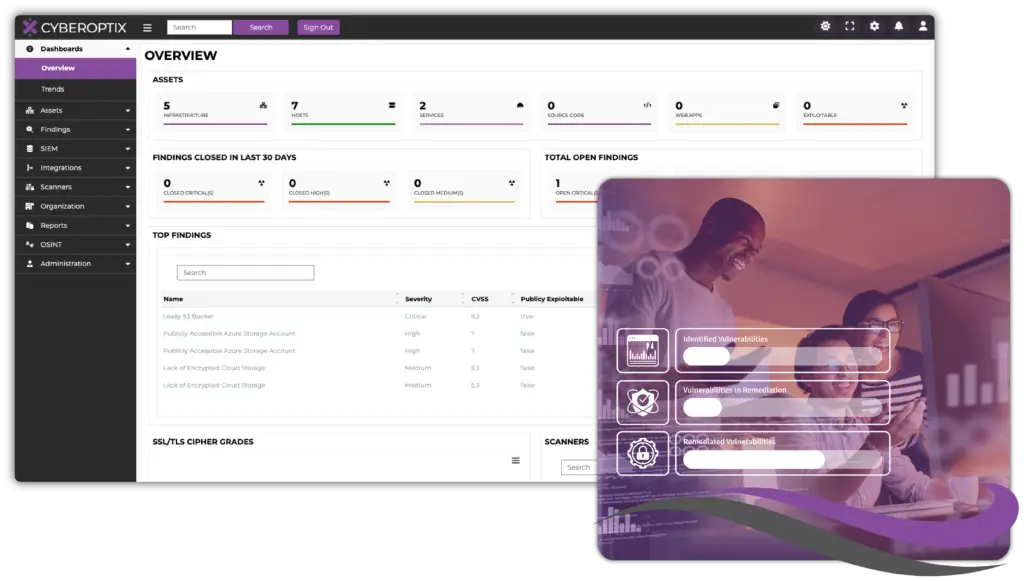
Make Vulnerability Identification and Remediation a Seamless Process.

Fragmented tools and workflows are among the biggest obstacles security teams face when managing vulnerabilities. Disjointed processes create blind spots, make it harder to prioritize threats, and often lead to inefficiencies that waste time and resources. Without a clear and centralized system, it’s nearly impossible to gain the visibility needed to protect your organization from evolving threats.
CyberOptix’s Penetration Testing Management License solve these problems by bringing everything together into one cohesive platform. By centralizing vulnerability discovery, prioritization, and management, our solution helps your team move from chaos to clarity. With clear task assignments and seamless workflows, your security team can focus on what matters most, identifying risks, prioritizing them effectively, and mitigating threats to protect your organization’s critical assets. The result is a more efficient, collaborative, and proactive approach to vulnerability management.
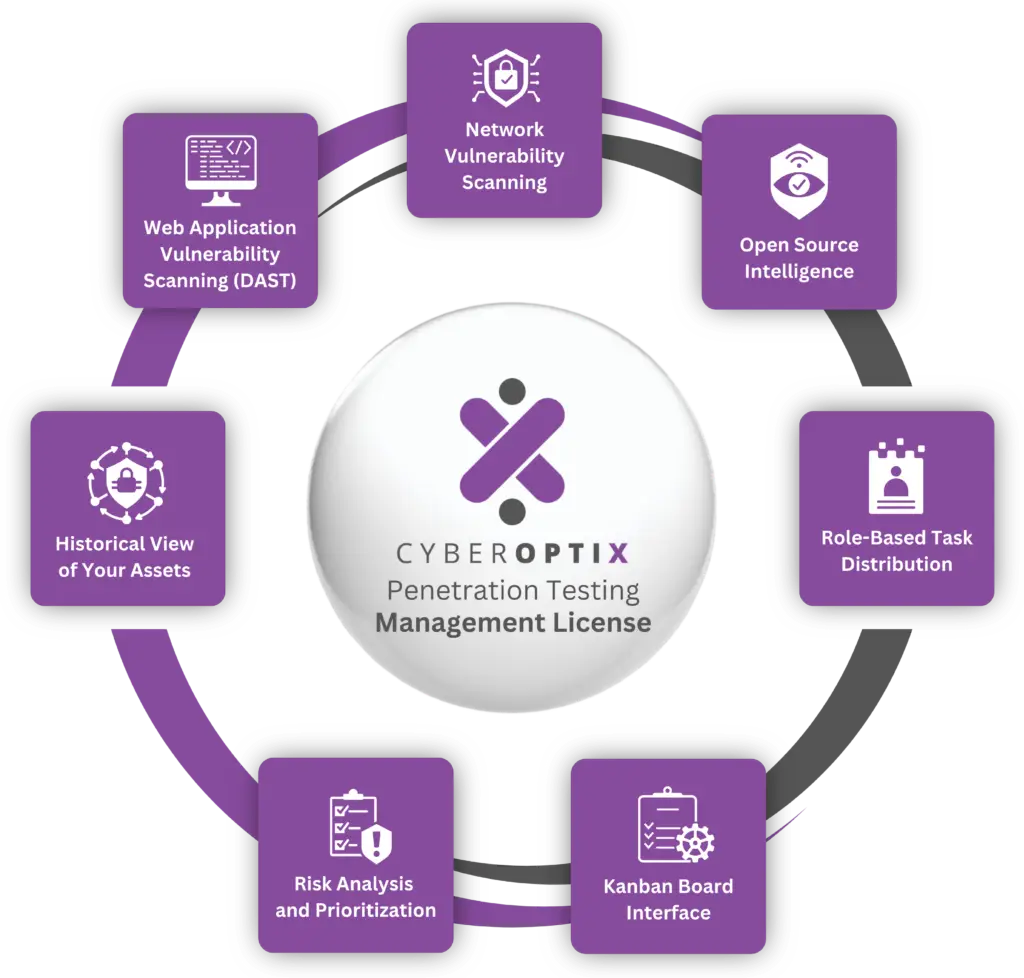
The CyberOptix Penetration Testing Management license provides a robust suite of tools and capabilities meticulously crafted to streamline and enhance vulnerability management and penetration testing processes. This license is designed to address the core challenges organizations face in identifying, prioritizing, and addressing vulnerabilities, ensuring a seamless and efficient workflow.
Dynamically scan web applications for security flaws during runtime, so your team can identify and mitigate vulnerabilities.
Continuously assess your network for weaknesses that attackers could exploit, delivering them to your security team to valiate and remediate.
Integrate with OSINT tools to consolidate publicly available information into one platform, enhancing your understanding of threats.
Assign tasks to specific team members based on their role, optimizing productivity and streamlining vulnerability remediation.
Organize tasks and track remediation progress visually on our kanban board interface, improving team collaboration and streamlining workflows.
Automatically categorize and prioritize vulnerabilities based on risk level, allowing your team to focus on resolving the most pressing issues.
Manage vulnerabilities from discovery to resolution, with features like a kanban board interface and role-based distribution designed to ensure nothing falls through the cracks.

Offensive teams rely on CyberOptix Base Features to lay the groundwork for effective vulnerability discovery and testing. By consolidating essential tools and processes, our platform provides the resources needed to identify and analyze potential weaknesses, enabling offensive teams to simulate real-world attack scenarios and refine their strategies.
Utilize network, host, and web application scanning to identify over 20 different types of vulnerabilities.
Organize discovered vulnerabilities using the kanban board interface, documenting potential attack methods.
Conduct asset discovery to understand relationships between exposed systems and potential pathways for attack.
Use tools like Metasploit and GVM to test how vulnerabilities could be exploited in live environments.
Gather OSINT and use publicly available data to build realistic and informed attack simulations.
Defensive teams rely on CyberOptix Base Features to proactively identify, understand, and address vulnerabilities within their environment. The platform enables defenders to assess potential exposure, prioritize remediation efforts, and gain a clear understanding of what attackers might exploit.

Use DAST and OSINT tools to uncover and plug publicly accessible vulnerabilities and exposed data.
Perform network and host scans to identify misconfigurations, out-of-date software, or exposed services.
Use asset discovery tools to gain a high-level overview of what an attacker might see, including connected devices, services, and weak points.
Assign and track remediation tasks with role-based distribution and kanban workflows to ensure vulnerabilities are addressed efficiently.
The CyberOptix Base Features License integrates seamlessly with top-tier platforms, including Microsoft Azure, AWS, Google Cloud, Cisco, Fortinet, Jenkins, Jira, CrowdStrike, and Red Hat. These integrations enable security teams to unify data from cloud, network, endpoint, and on-premises environments so they can run their vulnerability management program from a single platform.











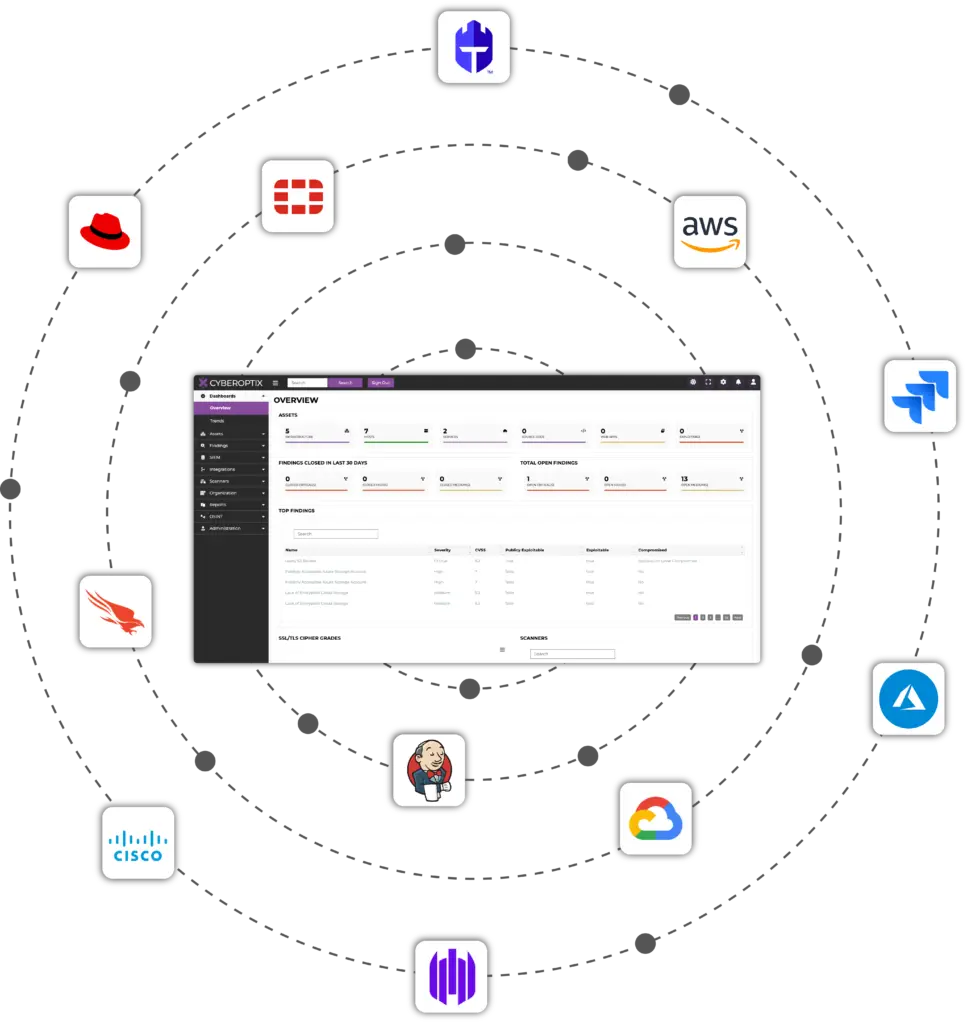
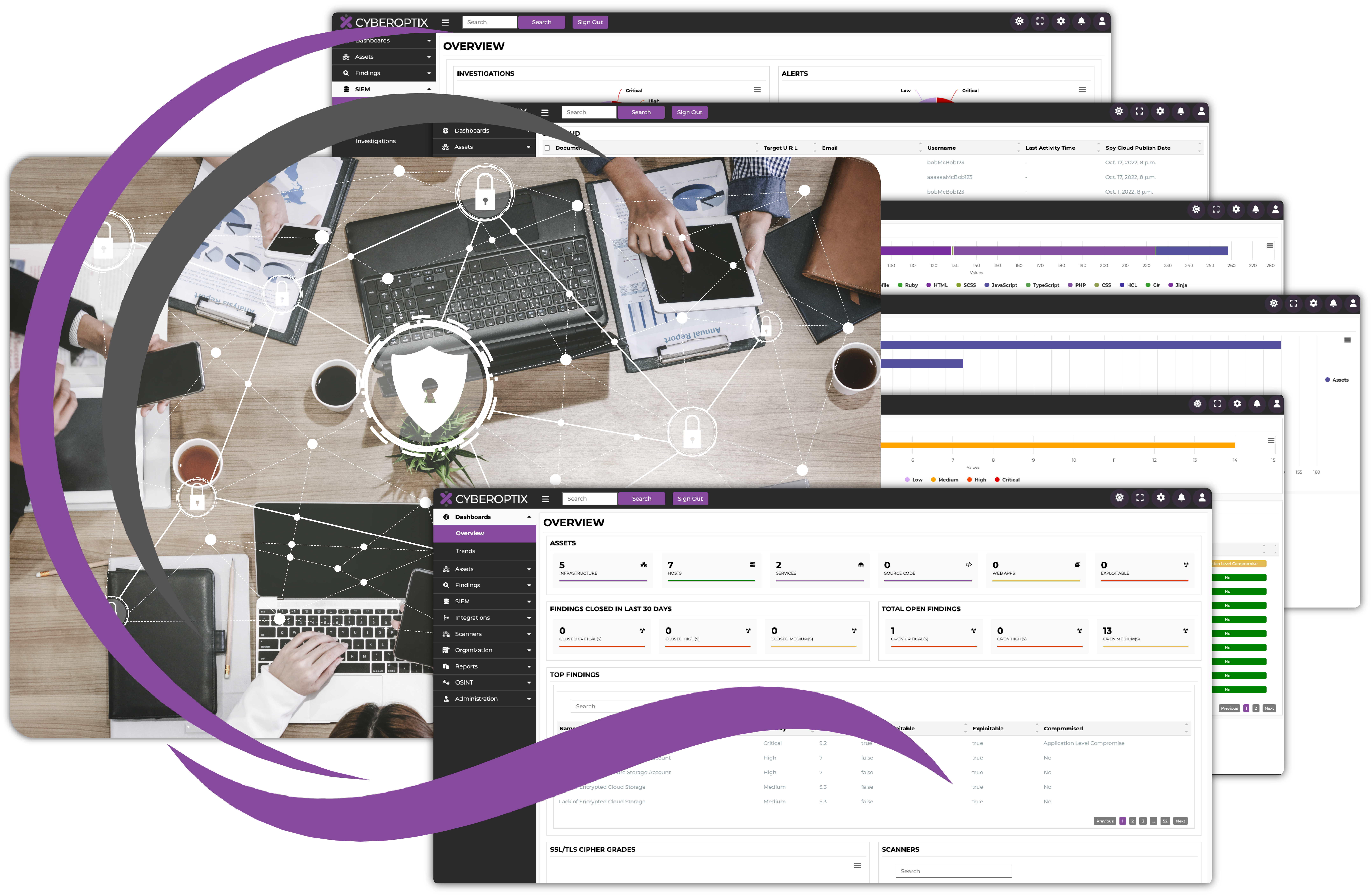
Beyond the capabilities included in the Base Features License, CyberOptix offers four other licenses that extend its functionality, empowering organizations to address even more threats and attack vectors from a single place. These features are designed to complement the Base Features License and provide a deeper level of insight, control, and adaptability.
CyberOptix’s Attack Surface Management License provides offensive teams with visibility into both internal and external vulnerabilities, allowing them to craft realistic attack scenarios.
Defensive teams use CyberOptix’s Attack Surface Management License to gain a comprehensive view of their attack surface, enabling them to identify and close security gaps proactively.
The CyberOptix’s SIEM License empowers offensive teams to conduct advanced simulations and test an organization’s defenses by leveraging real-time insights into logs and security events.
Defensive teams rely on CyberOptix’s SIEM License to gain real-time visibility into security events and logs, enabling them to detect and respond to threats with speed and accuracy.
Offensive teams leverage CyberOptix’s DevSecOps License to uncover application vulnerabilities with precision, enabling targeted and comprehensive penetration testing.
Defensive teams rely on CyberOptix’s DevSecOps License to seamlessly integrate security into the Software Development Lifecycle (SDLC), ensuring vulnerabilities are identified and mitigated early, before they reach production.
Offensive teams use CyberOptix’s Dark Web License to simulate real-world attack scenarios, leveraging intelligence gathered from dark web sources.
Defensive teams rely on CyberOptix’s Dark Web License to proactively address risks identified on the dark web, such as stolen credentials, vendor breach records, and executive exposure.
Don’t let disjointed tools and fragmented workflows slow your team down. CyberOptix’s Penetration Testing Management provides everything you need to discover, prioritize, and remediate vulnerabilities efficiently and effectively.
Contact us today to learn how CyberOptix can transform your vulnerability management strategy.